The cybersecurity market has hundreds or thousands of vendors competing for budget, all with different solutions to different perceived problems.
Faced with all that noise, cybersecurity teams face a huge challenge to understand their options—let alone make effective decisions.
In The Paradox of Choice, American psychologist Barry Schwartz argues that eliminating consumer choices can greatly reduce anxiety for shoppers. Bring that into the cybersecurity world, and you can add an extra dimension. Limiting choice for cybersecurity leaders doesn’t just minimize anxiety—it also improves results, as measured by the maintenance of acceptable service levels.
Returning to ITIL
It’s easy to forget how young the cybersecurity industry is. Although many of us have been working hard for a couple of decades to protect our organizations from cyber threats, our industry is still in its infancy compared to the more established field of IT operations.
In our last blog, What Can Cybersecurity Learn from IT?, we looked at the differences in how cybersecurity and IT operations teams set and achieve their objectives.
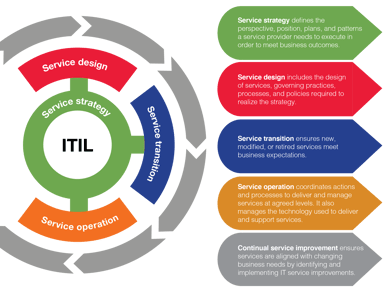
In particular, we focused on the ITIL framework, which is used by IT departments worldwide to help them meet business expectations and SLAs. ITIL emphasizes the importance of getting the basics right, and one of its core components is change management.
Change management follows a very simple process:
- Establish a trusted baseline of what’s allowed in our environment.
- Track and manage changes from that baseline.
Bring this concept into cybersecurity, and its benefits are clear. If we can establish a trusted baseline of what is allowed—files, users, processes, and so on—and then block everything else, we’ll be a long way towards maintaining the availability, integrity, and privacy of our systems, assets, and data.
However, before we get to that, we need to learn from another much older industry than our own.
Learning From Physical Security
One of the strangest things about cybersecurity compared to other disciplines is the focus on finding bad things and preventing them.
If that sounds strange, think about it like this. If you managed physical security for a building (e.g., a government office), how would you stop the wrong people from getting in?
Most likely, you wouldn’t try to track every single person who isn’t supposed to be in the building. That would quickly exhaust your resources and achieve essentially nothing. Instead, you’d build and maintain a list (baseline) of everybody who should be there and use a control system (probably ID cards and security guards) to ensure only those people are allowed in.
Of course, this system isn’t perfect. Sometimes, someone who was supposed to have access isn’t allowed in. This is easy to manage. The blocked individual simply tells the guard why they should be allowed in, and it’s quickly verified (or not). This process is called ‘managing by exception.’
Alternatively, some people will try to force their way in. Again, this is easy to manage by exception. The security guard will see the problem and apprehend them.
This approach runs contrary to most public discussions of cybersecurity principles.
Most cybersecurity controls use denylists to try to identify all possible ‘bad things’ and prevent them. Instead of maintaining a small database of things that are allowed, cybersecurity teams maintain a monstrous database of things that aren’t allowed and constantly monitor for them.
This approach is reactive, slow, and misses threats simply because they haven’t been seen before.
What's In A Trusted Authoritative Baseline?
A trusted baseline includes all the assets, file hashes, configuration settings, etc., allowed to exist in an environment. In addition to information determined by the organization, a baseline also includes best practices from authoritative sources like CIS Benchmarks and DISA STIGs.
Collectively, this information forms an organization’s trusted baseline. Once the baseline is set, the organization can monitor changes to ensure they comply with the baseline. If they don’t, they can either be blocked at the source, quickly remediated, or—if it turns out that the change is safe—accepted and added to the baseline.
5 Steps To Better Security Outcomes
Imagine how life would be for cybersecurity teams if we followed in the footsteps of traditional IT operations and service management. Consider this ITIL-inspired, basic approach to cybersecurity:
- Service strategy: Determine objectives for the security function
- Service design: Set a trusted, authoritative baseline of what you have (software, hardware, services, etc.) and what is allowed to be and happen in your environment.
- Service transition: Enforce the baseline by monitoring changes in the environment and blocking anything that isn’t explicitly allowed.
- Service operation: Carry out normal security operations to identify any threats or issues to make it past baseline enforcement.
- Continual service improvement: Learn from mistakes and make changes to the baseline.
This approach is achievable—and with far better results than most security teams have come to expect.
System Integrity Assurance (SIA)
System Integrity Assurance is a completely different approach to cybersecurity that focuses on the fundamentals. Instead of trying to identify and categorize all bad things, it instead identifies everything that is allowed in an environment—and blocks everything else.
Some level of management by exception is needed, of course. But fundamentally, SIA gives organizations complete control over what happens in their environment.
This begs another question:
What happens if you know every time something is added, removed, or changed in your environment, and you stop anything that isn’t authorized… and you expand this capability across all asset classes?
- Ransomware and other malware can’t run in the environment.
- Attackers can’t traverse the network or exfiltrate data.
- Nobody can change files or configurations to make them dangerous or non-compliant.
- Users can’t accidentally run malicious attachments.
- Nobody (even privileged administrators) can alter critical system files.
This approach takes away a massive proportion of the threats that can arise in an IT environment with minimal human involvement.
To find out exactly how integrity verification addresses the major issues in cybersecurity, download the Authoritative Guide to System Integrity Assurance.

November 17, 2021