CimTrak for Network Devices
Detect Unexpected
Network Configuration Changes
Network Configuration Changes
Benefits of Using CimTrak for
Network Devices
Network Devices
Detect change to the attributes of any member entity or configuration
Side-by-side comparisons to highlight changes
Restore a previous configuration when necessary
Eliminating unexpected network outages requires knowledge of what’s actually changing from an expected and trusted state of operation. CimTrak provides comprehensive visibility and analysis across your entire network for changes that are the result of malicious or unintentional activity. Whether it's authorized or unauthorized activity, CimTrak's change reconciliation capability can highlight a side-by-side comparison of what's changed. If change(s) are unwanted, CimTrak can take corrective action and restore to any number of previous baselines to ensure trust and resiliency enterprise-wide.
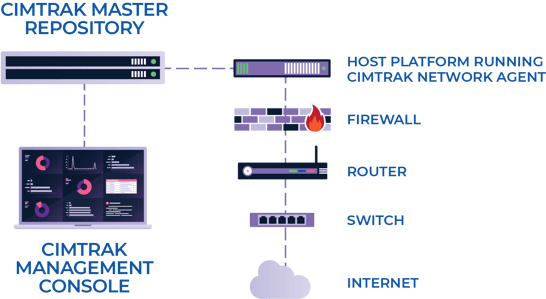
How CimTrak Works for Network Devices
A few examples of how traditional security tools would not detect or identify a problem resulting from malicious change(s) to Network Devices:
Action : The threat actor changes the hostname of the device
Impact: When the threat actor changes a hostname, it may not be recognizable by a human or system via DNS may no longer be able to communicate with it.
Action : The threat actor changes the device IP address
Impact: When the threat actor changes the device IP, it is no longer at the address the admins recognize. Any devices pointed to this IP will no longer be on the network or can communicate.
Action : The threat actor deletes all other users except the one currently compromised
Impact: When the threat actor deletes the other users, this prevents them from having a chance to defend against the threat actor.
Action : The threat actor changes the password of the compromised account in use
Impact: When the threat actor changes the password of the account in use, this prevents anybody from gaining admin access to the device ever again.
Action : The threat actor changes route tables
Impact: When the threat actor changes route tables, this changes the routes available for devices on the network to communicate properly.
Action : The threat actor changes interface configuration
Impact: When the threat actor changes interface configuration, any physical devices plugged into those interfaces will now have a different IP or configuration and/or may not communicate as expected.
Action : The threat actor changes firewall rules
Impact: When the threat actor changes firewall rules, they could open up ports facing the internet, providing many open doors into the network for more infiltration attempts and/or other threat actor collaboration.
Action : The threat actor changes the MOTD Banner
Impact: When the threat actor changes the MOTD Banner, they include a message letting the user know they have been hacked and demand a ransom.