CimTrak for Cisco
What We Monitor
Cisco IOS is the operating system that runs on Cisco routers. In addition to directing network traffic between networks, routers often perform certain security functions as well. The behavior and functionality of the router
CimTrak for Network Devices monitors the device configuration for changes, logs the changes, and then notifies the responsible parties of them.

How CimTrak for Cisco IOS Works
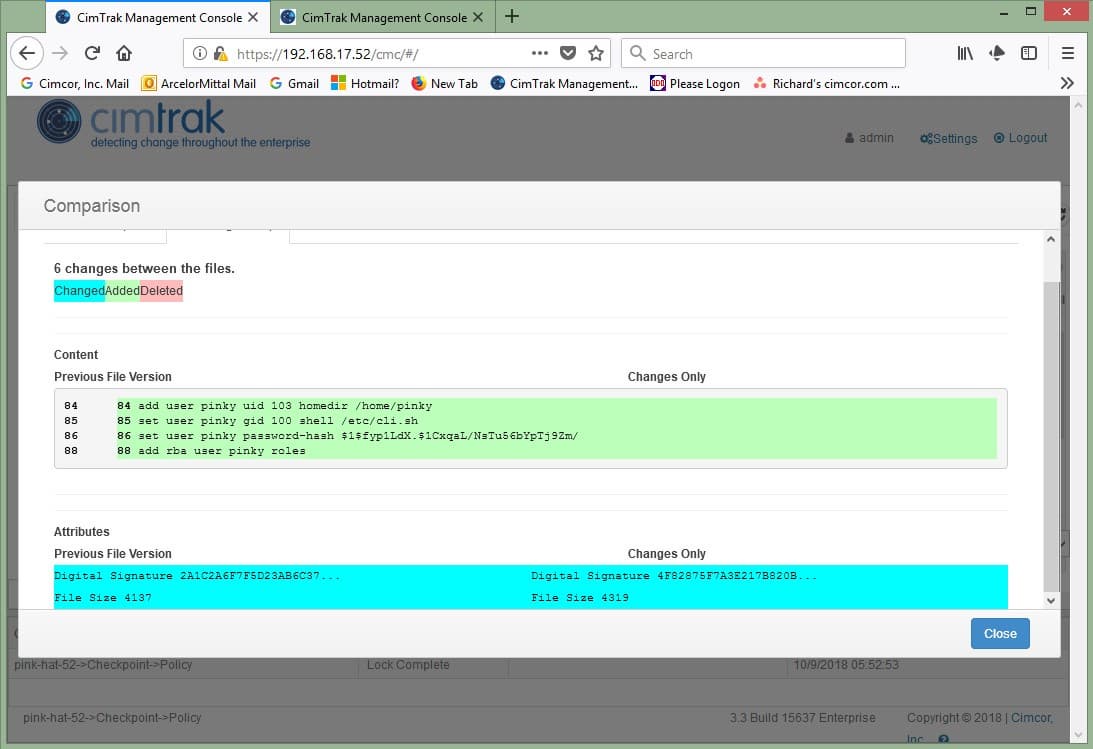
When CimTrak locks a Cisco IOS device for monitoring, it reads both the startup configuration and the running configuration of the device.
It calculates a digital signature for each of the
configurations, and stores them in CimTrak’s master repository along with a copy of the configurations.At user configured intervals, CimTrak reads the contents of both configurations, calculates the digital signature of each, and compares them to the signatures stored in CimTrak’s master repository.
When CimTrak detects a change in either configuration, that configuration and its digital signature
is then stored in the master repository.The master repository then logs the detected change and sends notifications to the configured emails and/or configured Syslog services and/or SNMP services.
CimTrak's seamless configuration with
Cisco IOS helps you create an audit-ready IT infrastructure.
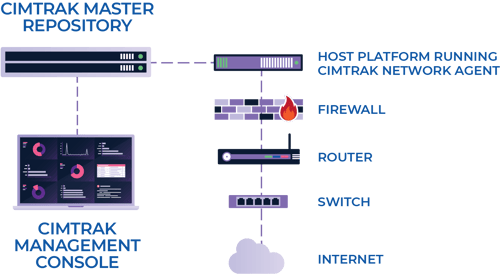
Why CimTrak for Cisco IOS?
CimTrak detects any change to the Cisco IOS device’s running configuration.
Here are some of the benefits of utilizing CimTrak for Cisco IOS:

Instantly Detect Changes &
Get Crucial Notifications

Get Real-time Remediation &
Restore Configuration
Real-Time Insight into Your Entire Network
See how your physical or cloud-based servers can stay protected in real-time