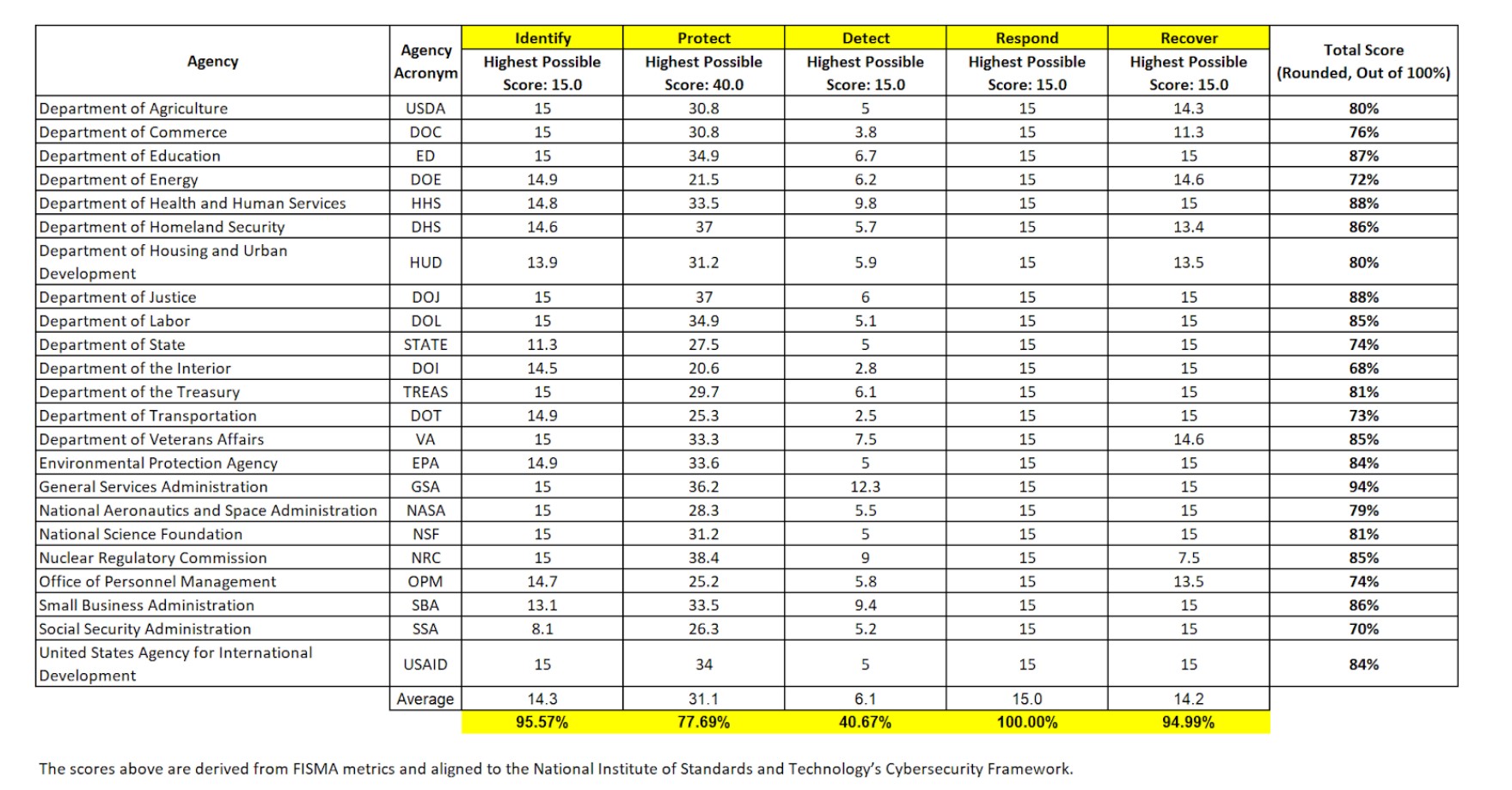
The Office of Management and Budget (OMB) and the Cybersecurity and Infrastructure Security Agency develop cybersecurity metrics – known as Federal Information Security Modernization Act (FISMA) metrics – to be used in the oversight of agencies’ information security policies and practices.
These metrics set forth a maturity baseline for cybersecurity to enable more informed, risk-based decisions and to achieve observable security outcomes. The cybersecurity scores below, derived from those FISMA metrics, represent the Federal Government’s progress in attaining EO 14028 milestones and implementing key cybersecurity measures.
The scores below are derived from FISMA metrics and aligned to the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (Identify, Protect, Detect, Respond, and Recover).
Cimcor Comments & Observations:
Respond and Recover categories are very mature verticals with technologies like SIEMs, back-ups, disaster recovery, and others to meet the objectives defined by NIST. Protect, as well, has had significant focus recently with the efforts and attention specific to Zero Trust (access/identity or aka authentication/authorization).
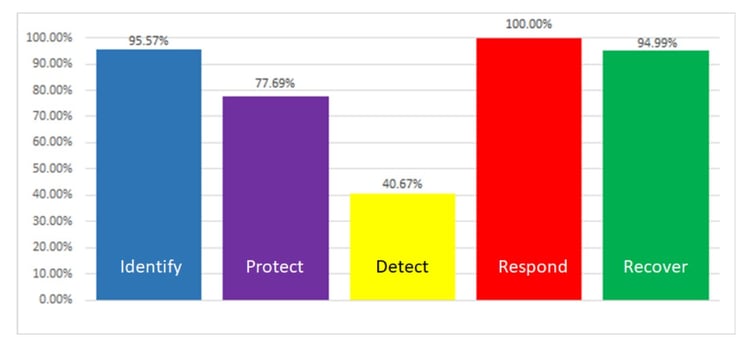
Detect (40.67% overall), however, is drastically behind and has been for years. Detect measures an agency’s ability to develop and implement the appropriate activities to identify the occurrence of cybersecurity events. We believe that the reason for this catastrophic number is the approach in which the government and industry are trying to “detect” malicious behavior. Detection of malicious activities, events, and behavior has been and continues to be through the lens of trying to understand, identify, and determine “bad” activities. This approach stems from the ubiquitous use of denylists, where organizations inherently trust that all activity is legitimate unless known to be malicious. Years of results show this will ALWAYS be reactive, as recent MTTI and MTTC industry figures support this argument.
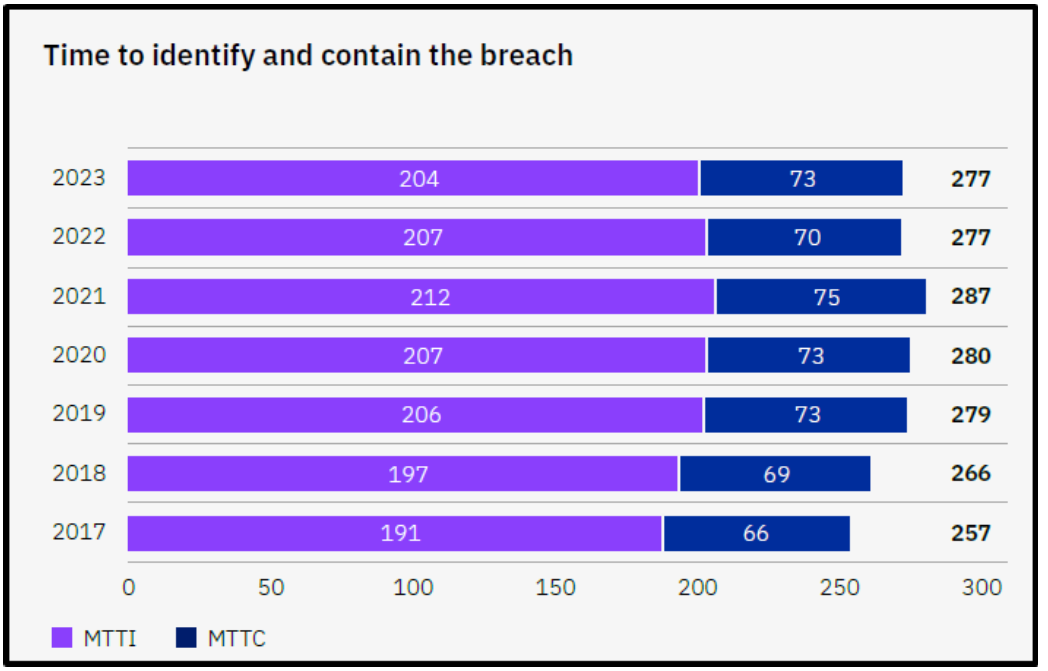
Shifting the paradigm from managing from a state of “bad” to “good” drastically changes Detect’s results. When a trusted baseline is established through best practices utilizing CIS Benchmarks and/or DISA STIGs and controlling the introduction of change on a real-time and continuous basis, it has the unique ability to highlight and pinpoint unauthorized change, which comes in the form of either malicious or circumvented change. Simply put, when observed change is reconciled with expected change, it immediately highlights unwanted, unexpected, and unauthorized activity in real-time… not 207 days.
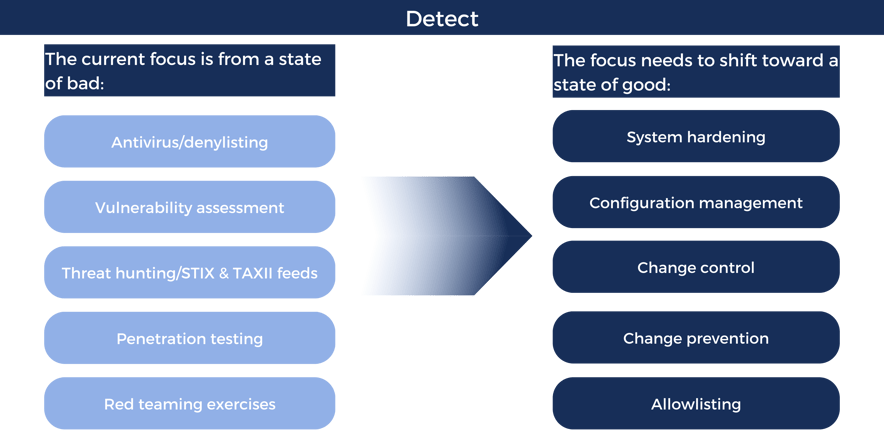
This approach can most impact the “Detect” capability of malicious activities and drive the current 40.67% average to a number north of 90%.
As mentioned earlier, unauthorized change comes in two forms (malicious or circumvented) and provides unparalleled value to security and operations. Two immediate examples include the FAA and the SolarWinds breach.
- Federal Aviation Administration - January 11, 2023, resulted from “self-inflicted” errors where engineers and system admins broke production systems by introducing unauthorized changes. If the approach detailed above were in place, the process to identify the circumvented change process would have been detected immediately. The change(s) could have been removed and restored in seconds, avoiding costly downtime and business disruption.
- SolarWinds – On March 23, 2020, SolarWinds inadvertently delivered back-door malware in its Orion software update giving bad actors the ability to gain access to manipulate systems by adding, modifying, or deleting files, configurations, ports, and numerous other settings to further compromise targeted devices and systems.
Cimcor Summary
The function of “Detect” needs to embrace a paradigm shift that manages information technology away from a state of bad/harmful to one that is understood and trusted (state of good). In doing so, the benefits of Detect functionality will be:
- Identifying unwanted and unexpected changes in seconds (malicious or circumvented)
- Immediately remediating and restoring unwanted and unexpected changes manually or automatically (restoring to a baseline…not a process of reprovisioning an entire image)
- Fewer security analysts are needed to deliver a more secure and protected infrastructure.
- Making IT audits easier by providing continuous evidence for compliance mandates.
The industry has also had a start/stop focus on integrity management for a variety of reasons. The disappointing fact is that all major best practice frameworks and compliance mandates call out “integrity” functionality without even really knowing that they are integrity controls by definitions. The closest the industry has come to knowing and understanding integrity management is File Integrity Monitoring (FIM) and Gartner’s Cloud Workload Protection Platform (CWPP).
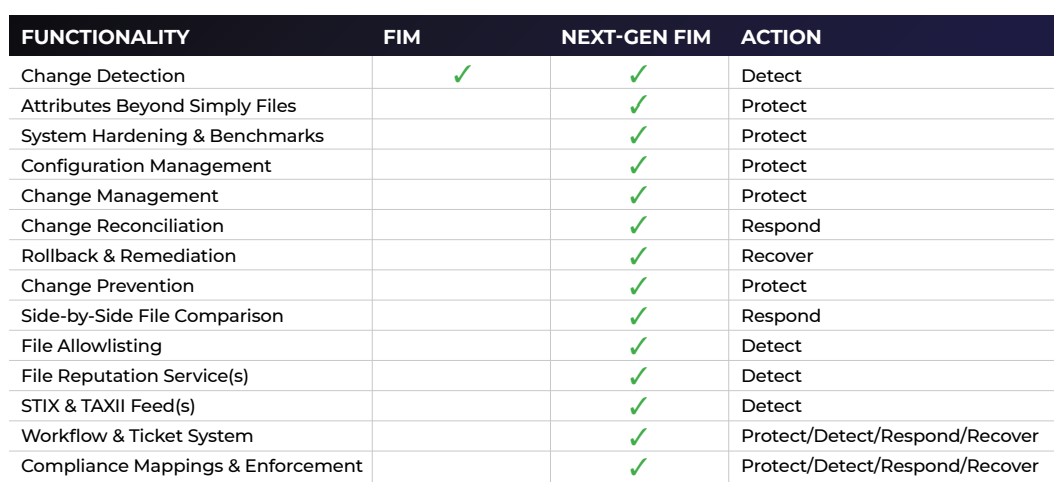
FIM
FIM’s awareness grew through compliance efforts initially driven by Sarbanes Oxley Act (SOX) in 2002 and PCI DSS v1 in late 2003. However, the title of File Integrity Monitoring is somewhat of an oxymoron and contradicts itself by the very use of the word integrity. FIM, by definition, is simply the detection of change from a baseline. There is no “integrity” in detecting change… it just tells you something changed from an expected state. While this is a step in the right direction, FIM still can’t tell you if the change was good or bad.
CWPP/WPP
Gartner, as recently as 2020, authored the Market Guide for Cloud Workload Protection Platforms, where integrity controls were called out as foundational and part of a core workload strategy. Almost a year after publication, Gartner renamed CWPP to Workload Protection Controls (WPC) as they realized the same detective controls are foundational, whether they operate in the cloud or on-prem environments.
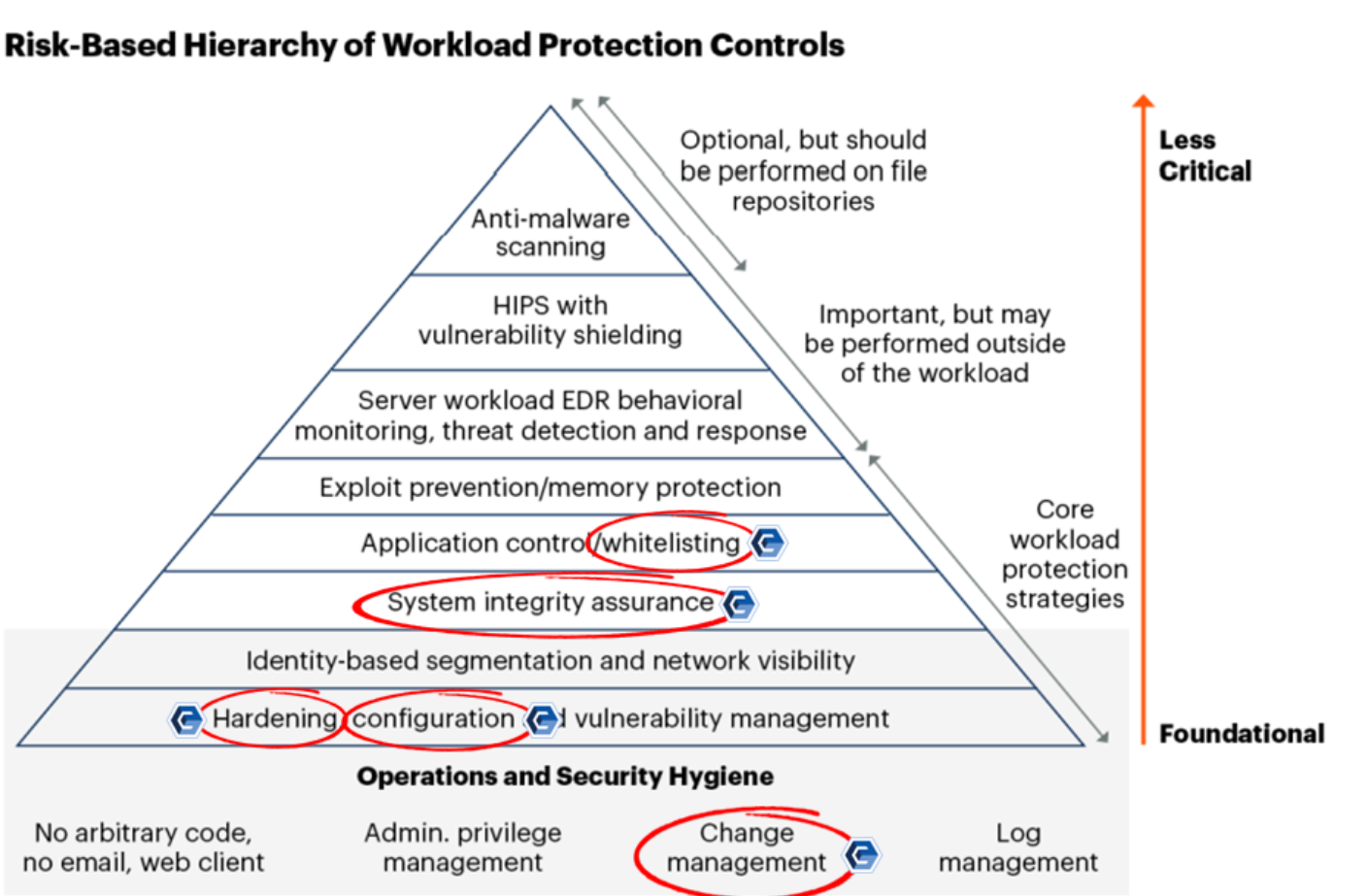
One possible cause for the lack of focus from a security perspective is that some integrity controls are inherently included and delivered by IT Service Management (ITSM) products and technologies. This confusion is likely why gaps and holes exist in security strategies and architectures, as seen with “Detect” in the Federal Cybersecurity Progress Report for Fiscal Year 2022. It’s time to bridge the gap, bring integrity controls into focus, and leverage them to improve security postures, mitigate ongoing risks, and detect security events in seconds versus the industry average of 207 days.
Tags:
FISMA
May 23, 2023


![4 Key Requirements for APRA CPS 234 Compliance [+ CHECKLIST]](https://www.cimcor.com/hs-fs/hubfs/APRA%20CPS%20234%20Checklist.jpg?width=520&height=294&name=APRA%20CPS%20234%20Checklist.jpg)

