Cimcor Webinars
Achieving DoD IL4/IL5 Authorization
Proven strategies for Secure, Compliant Cloud Operations
Many organizations pursuing DoD IL4/IL5 authorization don’t struggle because of a lack of effort; they struggle because the path isn’t clear.
For our first webinar of 2026, we are partnering with Schellman to unpack:
- The most common pitfalls that delay IL5 approval
- How to prepare for DISA’s rigorous assessment process
- Where integrity monitoring, baseline enforcement, and change control fit into continuous compliance
File Integrity Monitoring & Why It Matters
Real-Life Stories After Breaches & Lessons Learned
In this joint webinar featuring industry experts from Cimcor, Inc. and Stealth-ISS Group, Inc. you'll learn:
- Why file integrity monitoring can save your business from a major disaster (even if you have SIEM and EDR)
- Lessons learned from large incidents/breaches plus what could have been prevented, and more.
CimTrak & Zscaler's Integrated Approach to Zero Trust
In this joint webinar, learn how to strengthen threat detection, secure access, and maintain compliance by combining the real-time integrity monitoring of CimTrak with Zscaler's cloud-native security solutions. Explore practical use cases and see a live demo showcasing the integration of these technologies to protect your enterprise from evolving threats.
Together, these technologies help organizations build an effective Zero Trust security strategy.
CimTrak x Cisco Meraki: The Future of Security
The new, first-of-its-kind Cisco Meraki Module for CimTrak empowers organizations to monitor and be alerted for changes made on Cisco Meraki devices, providing unparalleled visibility and control over configurations.
See the live release of our latest module!
Using CimTrak & Stealth-ISS to Secure Critical Infrastructure
Of course, protecting your critical infrastructure is a priority when evaluating your cyber hygiene - and with cyber threats evolving daily, it is more important than ever.
Come listen to industry experts from Cimcor and Stealth-ISS discuss the latest strategies and technologies to help keep your infrastructure secure as possible.
WhatWorks in Reducing Compliance Costs and Increasing Resilience with Integrity Management Tools
In this SANS What Works report, SANS Director of Emerging Security Trends John Pescatore interviews Dan Schaupner, head of Digital Security Consulting North America for ATOS, to gain his insight on what he went through in the business justification and deployment of CimTrak's own file integrity monitoring software as part of reducing the cost of securely managing a large customer environment, as well as reducing the time and effort of demonstrating compliance.
Zero Trust & Tenet #5: Integrity Controls
What are integrity controls and who has defined them? Come listen to Dr. Chase Cunningham and Mark Allers discuss the importance and definition of integrity controls and how they ensure a foundation of trust at the workload layer for a trusted ZTA.
Top 3 Reasons You're Struggling with Security & Compliance
Join Robert Rodriguez and Justin Chandler in discussing the most pressing issues IT professionals face with compliance and security, including the key to continuous compliance with major regulatory requirements and how threat intelligence, reporting, and integrations help keep organizations secure.
CMMC SERIES PART 2: CIS Best Practices to On-Ramp, align and achieve CMMC compliance(ON-DEMAND)
Tony Sager, Senior Vice President and Chief Evangelist of Center for Internet Security discusses CIS Controls and how CIS best practices can help with CMMC compliance implementation. This LIVE discussion will feature a short presentation followed by Q & A regarding CMMC Compliance.
CMMC SERIES PART 1: A Comprehensive Overview of CMMC (ON-DEMAND)
Jeff Dalton of the CMMC-AB Board discusses with Cimcor "Everything You Need to Know About CMMC Certification". Dalton provides a short presentation addressing the three key topics of "Why", "How", and "When" followed by an entire session of Q & A.
CMMC Series Part 3: DIBs and CMMC Requirements: Simplifying the Continuous Audit Process with MSSPs (ON-DEMAND)
Dasha Deckwerth, CISO & Global Cybersecurity Consultant, discusses concerns regarding the audit process for CMMC requirements.
CMMC SERIES PART 4: Technical controls and requirements for Organizations
(ON-DEMAND)
In this webinar, LogRhythm and Cimcor discuss CMMC coverage with accompanying solutions and how those solutions can help augment compliance with CMMC at the various levels of certification. Additionally, Cimcor and LogRhythm discuss the considerations to make when using SIEM and FIM technologies for compliance.
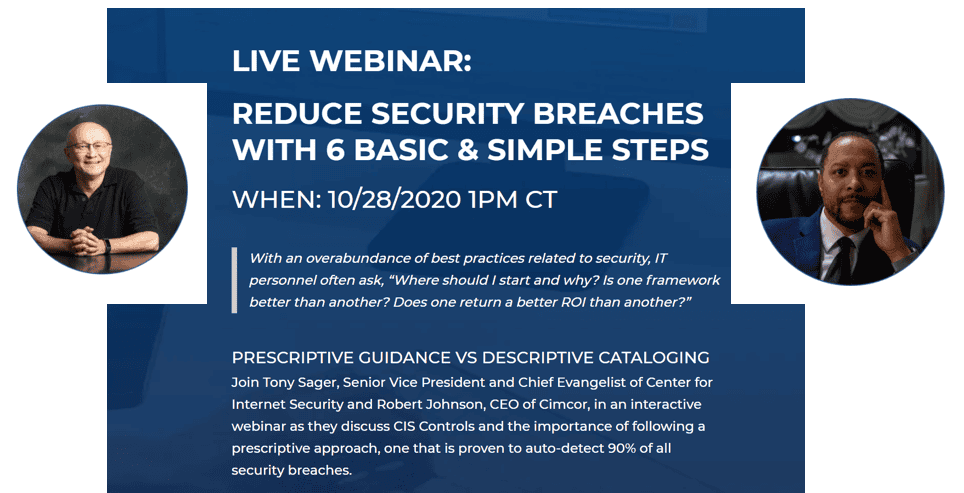
Reduce Breaches by 90% with 6 Simple Steps (ON-DEMAND)
Join Tony Sager, Senior Vice President and Chief Evangelist of Center for Internet Security and Robert Johnson, CEO of Cimcor, in an interactive webinar as they discuss CIS Controls and the importance of following a prescriptive approach, one that is proven to auto-detect 90% of all security breaches.
A Redefined National Approach to Cyber Resilience (ON-DEMAND)
In this webinar, co-hosted by CIS CyberMarket partner Cimcor, Mike Echols, former senior cybersecurity leader for U.S. DHS and author of Secure Cyber Life: The Government is Not Coming to Save You, discusses the need for a redefined national approach to cyber resilience. In this discussion, we pull the band-aid off and review the facts, which if embraced, may lead to meaningful national change.




%20(650%20x%20370%20px)%20(660%20x%20370%20px).png?width=660&height=370&name=Cimcor%20%2B%20Stealth%20ISS%20Webinar%20(650%20x%20344%20px)%20(650%20x%20370%20px)%20(660%20x%20370%20px).png)

%20(700%20%C3%97%20300%20px)%20(1)%20(1).png?width=800&height=344&name=Webinar%20(600%20%C3%97%20200%20px)%20(700%20%C3%97%20300%20px)%20(1)%20(1).png)
%20(2).png?width=800&height=344&name=Compliance%20Webinar%20CTA%20LP%20(1)%20(2).png)