The field of cybersecurity is facing a critical challenge that demands a paradigm shift in how we approach security. In a recent cybersecurity article by Renee Duddly of ProPublica titled "At What Point Does Profit Trump Safety?" the need for continuous education and a change in perspective is emphasized. Currently, we find ourselves in a constant state of cybersecurity chaos, chasing after every new solution that promises to solve the problem.
Unfortunately, the statistics and metrics of security breaches and hacks over the past decade clearly demonstrate that the problem is worsening, not improving. We have become desensitized to the constant stream of breach announcements, responding with quick fixes rather than addressing the underlying issues. In the case of Renee’s article, cybersecurity professionals call out Microsoft by stating, “Recent cyberattacks in the U.S. might have been detected sooner if infected computers had logging software”. However, this approach is akin to preventing airplane crashes by adding more data to the black box flight recorder.
The Industry-Wide Problem
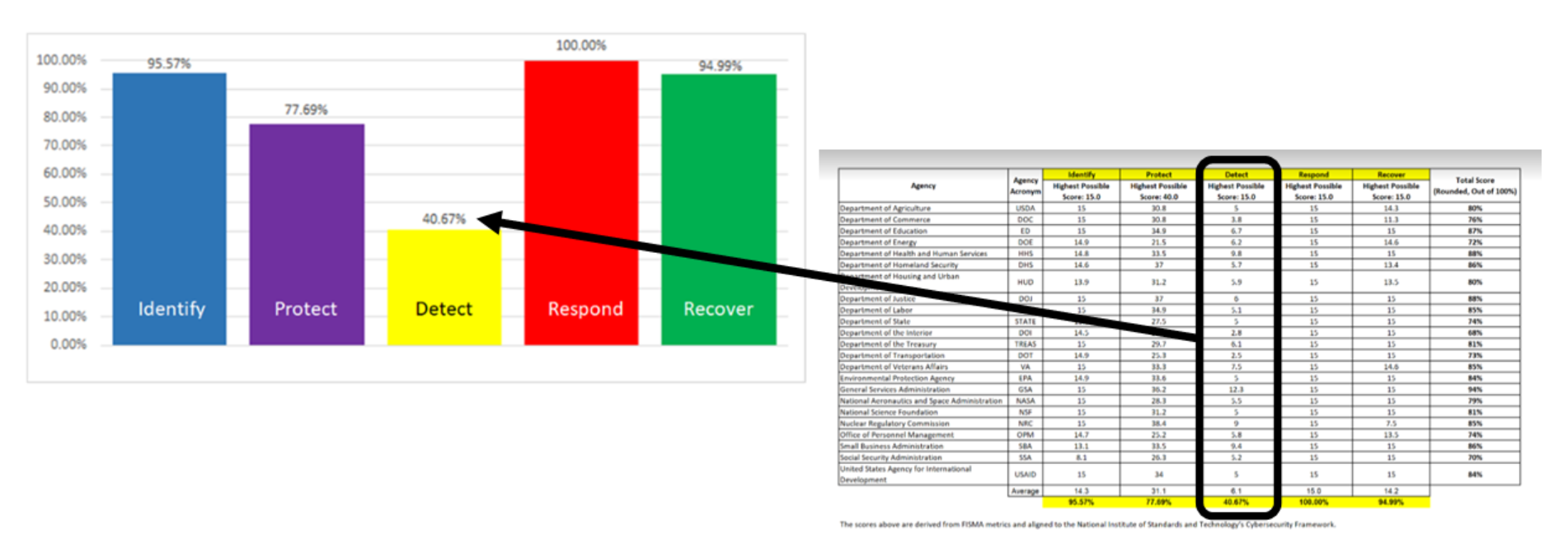
The Office of Management & Budget (OMB) and the Cybersecurity and Infrastructure Security Agency (CISA) recently released their 2022 Cyber Framework Report, which assessed the cybersecurity capabilities of 23 U.S. agencies in terms of identification, protection, detection, response, and recovery. To align this with NIST's Cybersecurity Framework, it is clear that Security Information and Event Management (SIEM) solutions primarily cater to response and recovery. These activities are reactive, initiated after an event has already occurred, meaning that the ‘Detect’ capability is what is sorely needed.
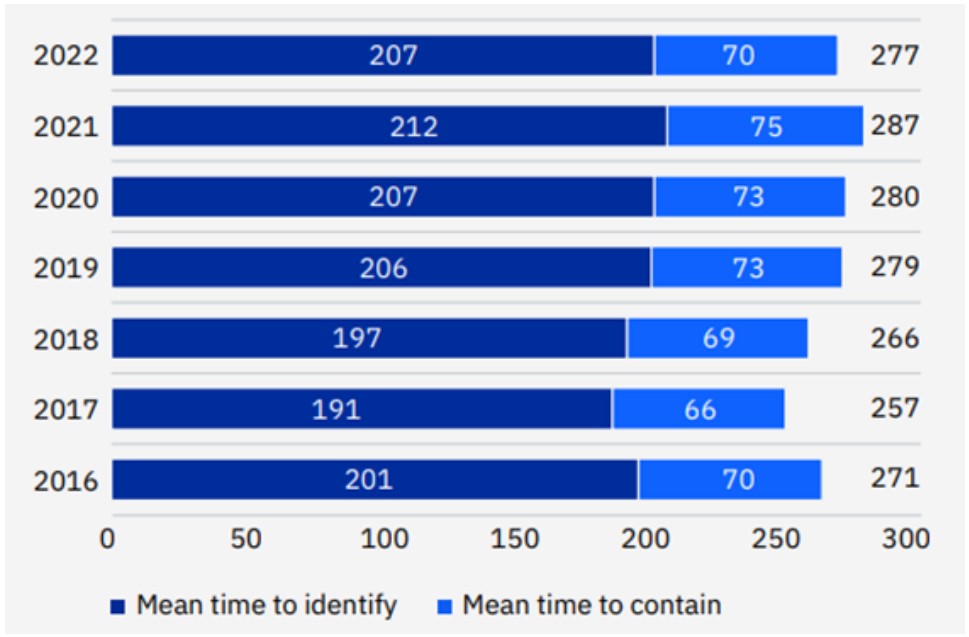
Ironically, the need for improved detection aligns not only with industry figures but also with Ponemon/IBM's Cost of a Data Breach Report 2022. The report uncovers the disturbing fact that breach detection, also known as Mean Time to Identify (MTTI), currently stands at a staggering 207 days, while response and recovery (containment) take an average of 70 days.
Drawing a comparison between for-profit software manufacturers and the automotive industry, Renee's article questions the point at which profit takes precedence over safety. While it is valid to consider software manufacturers' responsibility to minimize security risks, eradicating 100% of vulnerabilities resulting from bad actors, compromised open-source code, hijacked software updates, or compromised code signing is simply impractical.
Using a similar analogy, traditional IT security operates like a car with airbags but without brakes. We have focused heavily on containment and response, similar to airbags aiming to minimize death but often leading to extensive, time-intensive vehicle damage and repairs. Instead, we should prioritize the installation of brakes - detection capabilities - which can help us avoid catastrophic accidents and require only small yearly maintenance.
A Security Information and Event Management (SIEM) solution serves as an aggregation point for various data feeds, enabling analysis and potential identification of security breaches. By feeding better information into the SIEM, we can create a more trusted, secure, and resilient infrastructure. Most importantly, this data is binary, meaning there are no false positives, as the readings below will confirm.
Can The Problem Be Fixed?
So, can the problem be fixed? The answer is yes. However, the issue lies in the industry's failure to prioritize the critical IT security controls that were originally considered fundamental and essential. These controls have taken a back seat to less critical controls that receive more marketing attention. The Center for Internet Security (CIS), in its work on the Cost of Cyber Defense, provides a prescriptive approach that prioritizes foundational controls necessary for a safe and secure infrastructure. These controls consist of 18 categories with 153 safeguards, grouped into implementation groups 1, 2, and 3. Implementation Group 1 (IG1) has 56 safeguards and is considered the most basic and foundational set of controls, regardless of marketing propaganda, hype, or flare. Over time, controls that were once considered fundamental are now regarded as less critical, as observed in Gartner's guidance on Cloud Workload Protection Platforms.
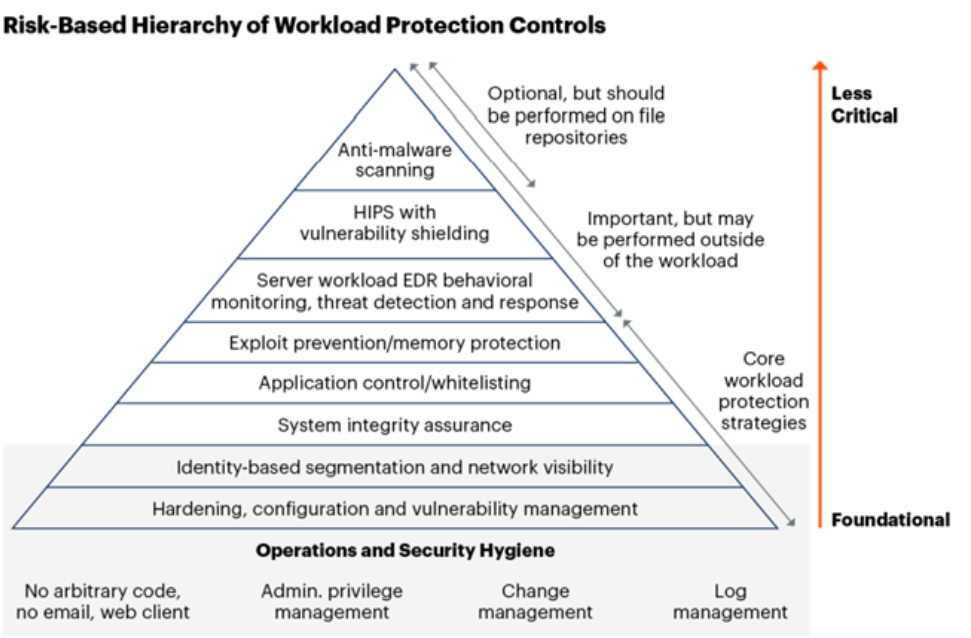
Interestingly, 36% (20 safeguards) and five of Gartner's core workload protection strategies align with "integrity controls,". These controls provide the foundation for transitioning from a reactive to a proactive security operation.
Reactive vs. Proactive Security Operations
Let's explore the difference between reactive and proactive security operations:
IT Airbags – Reactive Security Operations
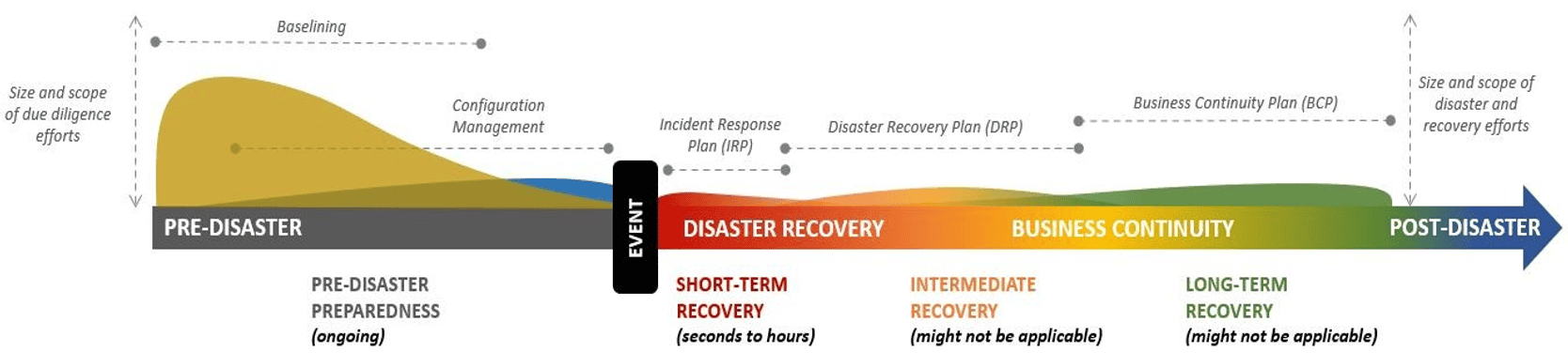
Reactive security operations (respond/recover), analogous to airbags in a car, focus on post-event activities and controls. These include Incident Response Plans (IRP), Disaster Recovery Plans (DRP), and Business Continuity Plans (BCP). However, these plans should be reserved for catastrophic events and not utilized on a daily or weekly basis, as outlined in ComplianceForge's report on Cybersecurity Supply Chain Risk Management (C-SCRM) Fundamentals.
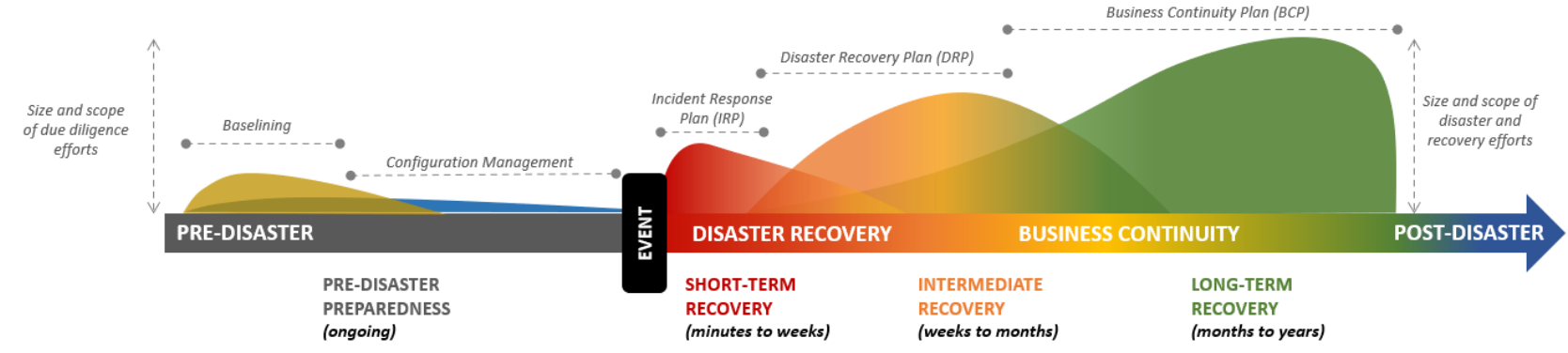
IT Brakes – Proactive Security Operations
Proactive security operations, similar to brakes in a car, prioritize pre-event controls that identify and detect unknown and unwanted activity. These controls involve system hardening, configuration management, and change management. When these controls are in place and functioning as intended, they minimize post-event activities and enable the detection of zero-day attacks. The IT Process Institute supports this notion, with data that shows that when these controls are in place, 91% of all security breaches can be auto-detected at the workload layer in their Change Configuration and Release Performance Study.
Related read: 4 Critical Proactive Cybersecurity Measures You Need in 2023
Why is 'Detect' Such a Problem?
The problem can be attributed to four factors:
- Most of the security industry focuses on response and recovery rather than detection.
- The ubiquitous use of denylists (aka blacklisting), where organizations inherently trust that all activity is legitimate unless known to be malicious.
- Use of antiquated technologies where companies continuously try to shove a square peg into a round hole.
- There is a need for improved education from credible organizations like SANS, especially concerning the role of and actions related to the "I" (integrity) in the CIA Triad.
The industry continues on this course because those with the largest marketing budgets tend to dominate mind share, and these budgets predominantly come from antiquated technology companies.
Leveraging Integrity Management & Assurance
Integrity management plays a crucial role in cybersecurity, but its meaning can be interpreted differently by different people. When discussing integrity management and assurance, most individuals immediately think of File Integrity Management (FIM), which involves detecting changes against a baseline. However, to be truly effective, we must determine if those changes are good or bad (planned or unplanned). This necessitates an understanding of all authorized and expected changes. By reconciling authorized changes with observed changes, we can promptly identify and remediate any unwanted or unexpected changes. Integrity management encompasses nine controls within a single workflow.
They include:
- System hardening
- Configuration management
- Change control
- Change reconciliation
- Change prevention
- Roll-back and remediation
- Allow-listing
- File reputation
- STIX/TAXII feeds
- Ticketing system and change authorization workflow
By assembling these controls into a structured workflow, a remarkable paradigm shift takes place. The OMB/CISA "Detect" rating, currently at 40%, can soar to a theoretical high of 90% or more, while the time taken to identify security breaches drastically reduces from 207 days to just 1 day. Achieving this transformation hinges on managing from a standpoint of distinguishing between good and bad states, incorporating integrity management capability and controls at its core.
Implement Proactive Security with Zero Trust
The drive for Zero Trust originates from the White House's Executive Order (EO) 14028, a response to the critical challenge of safeguarding sensitive data that directly affects our national and economic security. The primary aim of Zero Trust is to ensure that only authorized individuals gain access to specific information precisely when needed. This strategic approach revolves around implementing stringent controls for authentication and authorization (access and identity), and it remains the focal point of industry marketing.
Never Trust…Always Verify
However, Zero Trust extends beyond access and identity management. In NIST SP 800-207 Zero Trust Architecture, there are seven tenets, with Tenet #5 placing a particular emphasis on integrity. The rationale is clear – securing the workload is essential to establish trust and protect the application and data it supports. It is astounding that some security experts fail to realize that if a ransomware attack targets a Zero Trust implementation, it essentially nullifies the protection, leaving us back at the starting point. Once data is encrypted, Zero Trust cannot effectively mitigate the situation, rendering everything vulnerable once more.
Tenet #7 - The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
Solving Detection: How CimTrak Can Help
The CimTrak Integrity Suite*, developed by Cimcor, is a robust security, compliance, and integrity management tool that offers real-time integrity monitoring, assessment, and remediation of IT assets. Those capabilities include system hardening, configuration management, change control, change prevention, roll-back and remediation, allow-listing, file reputation, STIX/TAXII feeds, and a workflow that enables change reconciliation by comparing authorized changes against observed changes. This process has the unique ability to detect unknown, unwanted, and unauthorized changes (malicious and circumvented) in real-time and restore them to a previously trusted baseline of operation in seconds.
CimTrak monitors files, directories, configurations, ports, users, groups, policies, active directories, database schemas, cloud configurations, hypervisors, network devices, and more across numerous operating systems, devices, virtual environments, and cloud architectures. CimTrak can help an organization easily implement 800-53 Controls for SI, CM, AU, IR, SC, and SA and align with 22% of the control capabilities in the DoD Zero Trust Implementation Framework.
*Cimcor owns the patent on real-time change detection and remediation.
Tags:
Zero Trust
August 1, 2023




