CimTrak for Databases
Monitor Critical Database Objects and Settings for Changes
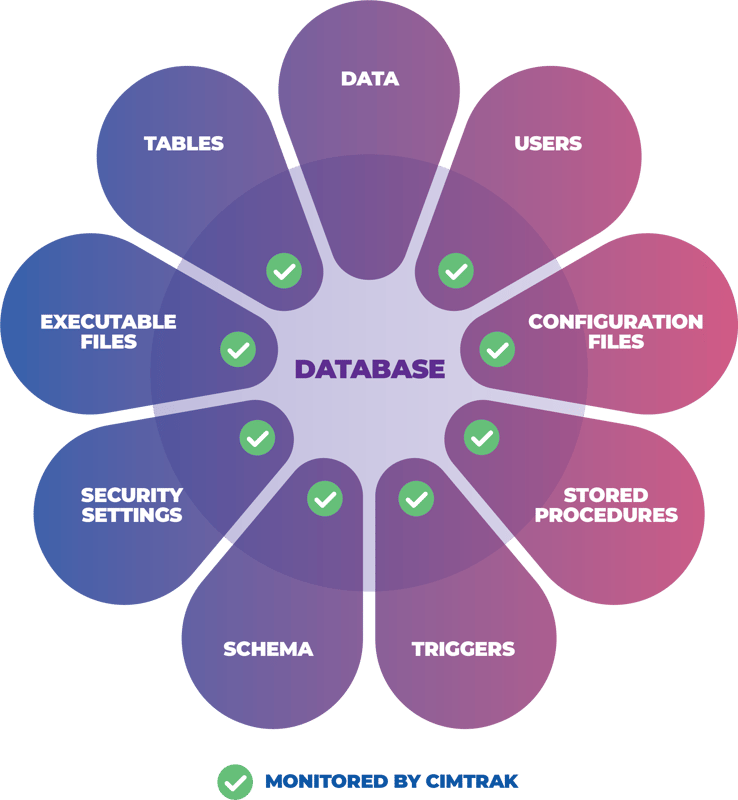
WHAT WE MONITOR




Managing the security parameters of databases might be one of the most overlooked security risks and vulnerabilities in today's environments. Many security professionals don't understand that a database consists of more than just 'data'... as a result, they don't understand the perceived threats and risks. CimTrak for Databases reports on all changes to critical database components and immediately alerts you to those changes.

Monitoring changes to critical database components is essential to ensuring the integrity of your data remains intact. By instantly detecting changes to configuration files, security settings, stored procedures, triggers, tables, users, schema, and executable files, you can take swift and corrective action to determine if a change was intentional, malicious, or accidental.
Benefits of Using CimTrak for
Databases
Databases
Detect change to the attributes of any member entity or configuration
Compare the entity's attributes to the entity's previous configuration
Restore a previous configuration when necessary
How CimTrak for Databases Works
As with all CimTrak components, CimTrak for Databases is centrally configured and managed via the CimTrak Management Console. This means that, just like other CimTrak components, it is simple to configure and use in addition to being very cost-effective.
Active monitoring of database configurations and access settings is an important aspect of database management as well as an overall best practice in the IT environment. Database monitoring is an essential component of your IT security strategy that allows you to conduct monitoring without requiring a tedious, time-consuming, manual audit process.
E-commerce System
Action by Threat Actor
Threat actor modifies stored procedure that handles orders.
Adds the Following Logic
FOR A SPECIFIC CUSTOMER ID (the hacker's account), CHANGE THE PRICE TO $0.00 FOR EACH ITEM BEING PURCHASED.
Impact
This allows the threat actor to purchase everything he wants from the e-commerce provider for free.
Healthcare System
Action by Threat Actor
Hacker creates a new database user and grants admin privileges to this user.
Impact
The hacker is able to view and modify health records without limitations.
Compliance
CimTrak Compliance Orchestration can scan SQL Server and Oracle databases to ensure they are in a hardened state of operation. In the event of a failed scan, CimTrak will provide the description of the assessment, rationale, impact of the failure, references to the authoritative source(s), the specific benchmark used, what the actual value should be, and the prescriptive steps to remediate.
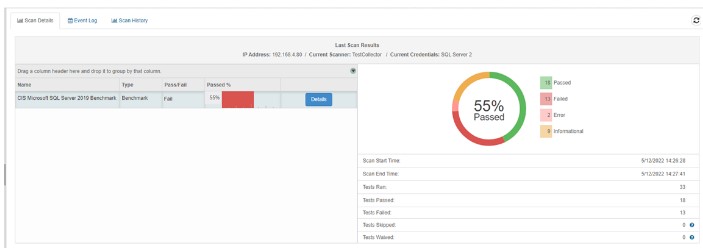
Active monitoring of database configurations and access settings is a critical aspect of database management and a general best practice in the IT environment. It allows you to monitor without requiring a tedious, time-consuming, and manual auditing process.
CimTrak for Databases is extremely cost-effective as well as simple to install, configure, and manage.