Why is SOX important? The main reason—it’s the law. Public companies are held to a higher level of accountability under financial regulations to ensure the integrity of the data-handling processes and financial statements through annual audits.
Compliance with Sarbanes-Oxley is notoriously difficult, resource-intensive, and expensive. In a recent survey, there has been a surge in the number of smaller companies spending $2 million or more a year on SOX compliance. Not to mention, 53% of companies have spent more time working toward SOX compliance from 2021 to 2022 than in previous years. While the costs can be significantly lower for many other companies, SOX is rarely cheap or straightforward.
Compliance managers and IT security professionals need tools to simplify meeting SOX compliance requirements, particularly data security and monitoring. If you're curious whether SOX controls specifically require file integrity monitoring (FIM) or system integrity assurance, the answer is yes. Join us as we review exactly where FIM and general integrity requirements fit into the SOX guidelines. We will also explore the connection between SOX and the Control Objectives for Information and Related Technologies (COBIT) framework, along with file integrity monitoring, which is a framework created by the Information Systems Audit and Control Association (ISACA). The specific purpose of COBIT is to help IT managers align business risk and technical requirements with best practice control requirements.
What is SOX Compliance?
The Sarbanes-Oxley Act of 2002, also known as SOX or the Public Company Accounting Reform and Investor Protection Act, is federal law. It establishes accountability criteria around financial and accounting operations. Organizations required to comply with SOX include U.S.-based companies with a public board and public accounting firms.
Significant Sections of the SOX Act Specifically Address:
302: Corporate Responsibility for Financial Reports
This section focuses on designating responsibility within the corporate structure. Based on the language of Section 302, the CEO and CFO are both responsible for:
- Reviewing financial reports
- Avoiding misrepresentation in financial reports
- Fairly presenting information in reporting
- Internal accounting controls
- Reporting accounting control deficiency or fraud
- Reporting changes in accounting controls
404: Management Assessment of Internal Controls
All financial reports must include an internal control report, which includes a control structure assessment by senior management. Registered external auditors must also evaluate the accuracy of internal controls.
409: Real-Time Issuer Disclosures
This section designates the requirement for regular disclosure of changes in financial conditions or operations.
902 & 906: Attempts & Conspiracies to Commit Fraud Offenses
Based on the language of these requirements, it is a criminal offense to alter information in reporting. It is also criminal to interfere with information availability requirements. Criminal penalties for certifying fraudulent reports can include up to $5 million in fines and 20 years in prison.
What Does SOX Say About File Integrity Monitoring?
While SOX Section 404 dictates several forms of "internal control" over-reporting, there is a lack of specific detail on what organizations should implement. Guidelines language specifies "performing fraud risk assessment" and preventing "management override of controls," but does not designate the tools or means organizations should use to achieve these ends.
As a result, SOX guidelines have shaped the COBIT framework, a set of guidelines for organizations that need to "comply with increasing regulatory compliance demands and [reap] the benefits of managing risk effectively." This complementary framework provides more insight into the types of controls against management intervention and fraud that support organizations' compliance efforts.
What is the Basic Structure of COBIT
COBIT 2019 is the latest ISACA version derived from COBIT 5. COBIT 2019 has adopted a structure that includes three major elements called the COBIT Cube:
- Business requirements include metrics of integrity, effectiveness, efficiency, confidentiality, availability, compliance, and reliability.
- IT resources consider applications, infrastructure, information, and people.
- IT processes consider domains, processes, and activities.
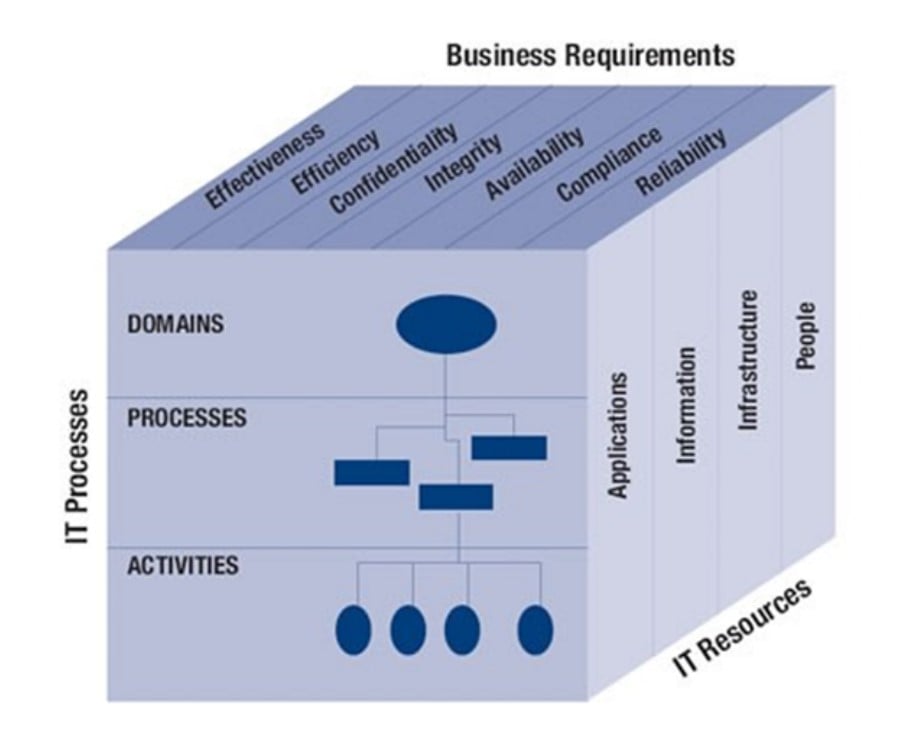
Source: ISACA®, COBIT® 2019 Framework: Introduction and Methodology, USA, 2018
All the IT processes are categorized under two objectives with five domains, also known as the COBIT Core Model:
Governance Objectives
- EDM: Evaluate, Direct, and Monitor
Management Objectives
- APO: Align, Plan, and Organize
- BAI: Build, Acquire, and Implement
- DSS: Deliver, Service, and Support
- MEA: Monitor, Evaluate, and Assess

Source: ISACA®, COBIT® 2019 Framework: Introduction and Methodology, USA, 2018
To help simplify COBIT 2019, there are essentially 35 core Objective ID families with 40 IT processes and controls described within governance and management objectives.
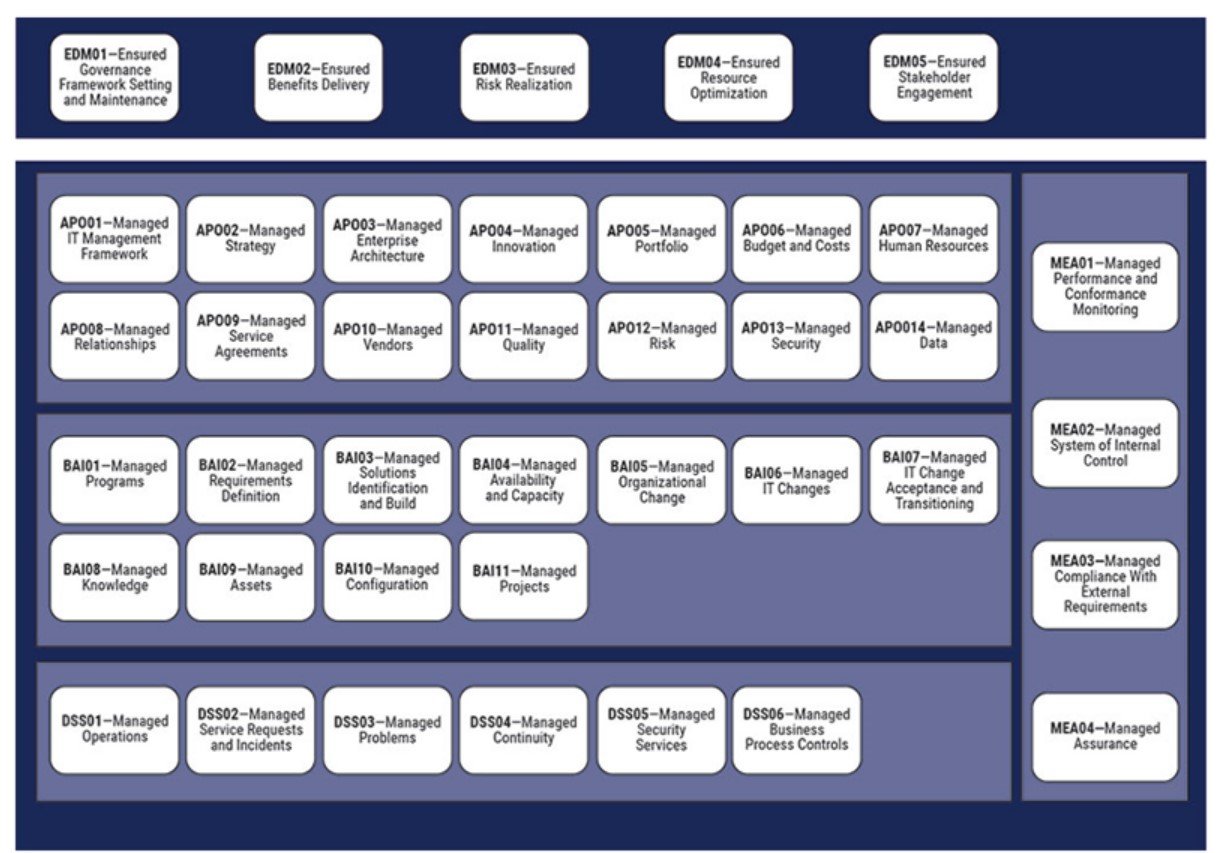
Source: ISACA®, COBIT® 2019 Framework: Introduction and Methodology, USA, 2018
What Does COBIT Say About Integrity and File Integrity Monitoring?
First, let’s ensure everyone is on the same page regarding integrity and its definition.
Cimcor defines integrity as encompassing:
- Controls
- A process to ensure that the controls are not only in place but also operating as expected.
Neither COBIT nor SOX specifically addresses file integrity monitoring in exact language. However, the general functionality of FIM is included, by basic IT definition, within some of the 40 COBIT processes.
So, what do integrity controls look like? Cimcor describes system integrity assurance, which includes the basic functionality of FIM and other integrity functionality, to include the following:
- Change Control
- Configuration Management
- System Hardening
- Change Prevention
- Roll-back and remediation (to a trusted baseline, NOT to be confused with reprovisioning...these two are very different!)
- File Allowlisting
- File Reputation Services
- Digesting STIX/TAXII Feeds
- A workflow and ticketing system where the detection of change is the trigger that kicks off a process that includes the functionality of 1-8.
Coupling 1-8 with a closed-loop workflow process (#9) enables COBIT practitioners to achieve the fundamental business requirements of integrity while reaping the benefits of increased availability, reliability, and ongoing compliance.
Neither COBIT nor SOX specifically demands that organizations acquire file integrity monitoring. However, they point to a fair number of requirements closely tied to system integrity assurance or a sophisticated FIM. A few COBIT samplings include:
BAI 06 – Managed IT Changes
Objective: Manage all changes in a controlled manner, including standard changes and emergency maintenance relating to business processes, applications, and infrastructure. This includes change standards and procedures, impact assessment, prioritization and authorization, emergency changes, tracking, reporting, closure, and documentation.
Objective Purpose Statement: Enable fast and reliable delivery of change to the business. Mitigate the risk of negatively impacting the stability or integrity of the changed environment.
BAI 10 – Managed Configurations
Objective: Define and maintain descriptions and relationships among key resources and capabilities required to deliver I&T-enabled services. This includes collecting configuration information, establishing baselines, verifying and auditing configuration information, and updating the configuration repository.
Objective Purpose Statement: Provide sufficient information about service assets to enable the service to be effectively managed. Assess the impact of changes and deal with service incidents.
DSS 02 – Managed Service Requests and Incidents
Objective: Provide timely and effective responses to user requests and the resolution of all types of incidents. Restore normal service; record and fulfill user requests; and record, investigate, diagnose, escalate, and resolve incidents.
Objective Purpose Statement: Achieve increased productivity and minimize disruptions through a quick resolution of user queries and incidents. Assess the impact of changes and deal with service incidents. Resolve user requests and restore service in response to incidents.
Other Objective IDs that align with system integrity assurance controls and processes include:
- APO12
- APO13
- APO14
- BAI05
- DSS03
- DSS04
- DSS05
- DSS06
- MEA03
- MEA04
For modern finance and organizational leaders, system integrity monitoring and FIM software can support several COBIT controls to ensure data quality, protect against management intervention and fraud, and continuously maintain compliance 24/7/365.
How CimTrak Supports SOX Compliance
SOX demands near real-time acknowledgment of "changes," which requires applications and tools that support situational knowledge of your data and processes. A system integrity assurance tool provides real-time insight into your organization's IT resources (application, information, infrastructure, and people) to provide situational awareness and continuous understanding that your IT processes are followed and in compliance with SOX.
Integrity alerts provide binary notifications (no false positives) and alerts about unexpected changes so that organizations can verify that their assets are not subject to unauthorized access or modification. In addition, system integrity assurance can provide non-repudiation and unalterable audit trails of the change management process. CEOs and CFOs can then take comfort in reporting a security posture without fear of the threat of insider abuse or information modification. If unwanted change(s) occur, system integrity assurance can quickly assess and remediate in real-time to ensure that data integrity is protected in accordance with SOX requirements.
To learn more about how CimTrak supports SOX compliance, click here.
Tags:
Compliance
May 1, 2025


![4 Key Requirements for APRA CPS 234 Compliance [+ CHECKLIST]](https://www.cimcor.com/hs-fs/hubfs/APRA%20CPS%20234%20Checklist.jpg?width=520&height=294&name=APRA%20CPS%20234%20Checklist.jpg)

