Living in a digital era where every individual is becoming more dependent upon computing power, there is no question as to why the digital space has become such a desirable target for cybercriminals. At the beginning of 2017, Forbes noted a prediction of cybercrime costs to possibly reach $2 Trillion by 2019.
Cybercrime Costs
Since 2015, Symantec has reported that cybercrime victims spent $126 billion globally and spent an average of 19.7 hours dealing with cybercrime. Currently, as many as 3,617 data records are lost or stolen every minute. Though not all breaches are the same, the financial services and healthcare industries are the top two industries with the highest average global cost of a data breach per lost or stolen record, according to the 2017 Ponemon Cost of a Data Breach Report.
As we noted in a previous post, finance and healthcare are the two industries in which customers are most likely to take a hike after notification. With average turnover rates of nearly 7% reported by Ponemon, this is double the multi-industry average of 3%.
Who is Affected
Overall, the average organizational cost of data breach varies per country as reflected below.
The chart shows the average total cost of a data breach (measured in US$ millions) compared to the four-year average. Grand average for FY2017=$3.62, FY2016=$4.00, FY2015=$3.79, FY2014=$3.50
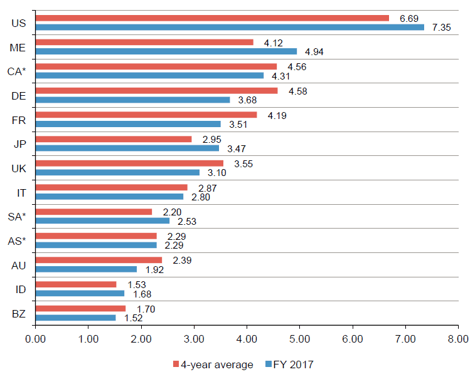
Source: Ponemon, Cost of Data Breach Study
*Please note: historical data are not available for all years.
Ponemon notes that the ease and availability of malicious exploit kits existing today may also be turning cybercrime into a business opportunity. In fact, according to Dan Turkel, competition among cybercriminals has become so fierce that they have begun to offer customer service, service guarantees, and other perks for customers. These types of services could be alluring for prospective and current hackers who are relatively inexperienced and incapable of developing their own malware. Looking at the increasing frequency and volume of cybercrime happening daily, it is apparent the number of new cybercriminals is growing as well.
How to Combat Cybercrime
In fighting against cybercrime, there is not a "one model fits all" for organizations. However, there are certain factors that could increase or decrease the cost of data breaches. And as CSOOnline points out, data is king and continues to remain the primary target of hackers.
According to Ponemon Institute, a fully functional incident response team reduced the cost of data breach by $19 from $141 (average) per record to $122 per record.. In contrast, third party involvement in the cause of the data breach resulted in an increase of $17, from $141 to $158 per record.
Source: Ponemon, Cost of Data Breach Study
INCIDENT RESPONSE TEAMS
Unfortunately, organizations many times do not learn how to handle an incident until after an attack has occurred. And as we have learned from recent breaches and Poneman's Overview, the longer it takes to identify a data breach, the higher the cost.
An effective incident response plan is vital to the health and security of the organization. Having access to an internal or outsourced incident response (IR) team has been the “top cost-reducing factor” for three years running as noted by Security Intelligence. Though organizations with a strong incident response team have the potential to reduce the cost of compromised records by close to $20 per record, Ponemon and Whitmore remind us of a set of valuable statistics.
- The odds of getting struck by lightning is 1 in 960,000.
- The odds of dating a millionaire is 1 in 220.
- The odds of experiencing a data breach is 1 in 4.
The 2016 SANS survey noted that 71 percent of respondents had incident response operations in the United States and 66 percent had teams in Europe and Asia, an increase from the previous year. This growth signifies global awareness of cyber threats, as well as greater investment and appetite for strengthening cybersecurity.
What Will the Future Hold
This year has seen improvement in reducing the mean time to identify and contain (MTTI & MTTC) data breaches from 201 to 190.7 and 70.1 to 66.2 days, respectively. However, the fact remains; those who were breached had an attacker within their system for more than 6 months before an incident response team identified the breach.
As emergency workers, the incident response team frequently deals with high-impact risk events which require specialized, trained personnel and highly organized collaboration. Time, communication, and decision-making are highly sensitive elements in emergencies. Having specialists on the team who have experience and expertise may result in far more efficient incident handling. Staffing for incident response teams faces the same shortage issues and lack of skill-set as the rest of the departments needing cybersecurity resources.
Frost and Sullivan's research reported a global shortage of the cybersecurity workforce to exceed 1.5 million unfilled positions by 2020. Another impediment to effective incident response IR is the lack of visibility across systems and domains. Every day, security workers are bombarded with a flood of alerts, network data, and account logs from tools and detection systems.
File Integrity Monitoring for Incident Response Teams
file integrity monitoring tool can be an asset to not only infosec programs but to the incident response team as well. From mitigating human-related and administrative risks to unauthorized access prevention, the most sophisticated file integrity monitoring tools can significantly free security resources and enable quick detection when safeguards fail.
Want to learn more about the State Of Cybercrime? Download the Cimcor 2017 State of Cybercrime today.
Tags:
Cybersecurity
October 10, 2017