Do modern information security professionals really understand what they're facing? The newly-released 2016 Verizon Data Breach Investigation Report (DBIR) took a deep dive into examining the data surrounding over 100,000 information security incidents in the past year. The results of their analysis ranged from surprising to not-so-shocking.
What is the Pulse of Information Security?
Today's cybercriminals are smart and effective, but they're often focused on long-standing, known vulnerabilities as a way to maximize their payload with minimum effort. This trend is fantastic news for organizations that invest in minimum forms of effective risk mitigation such as employee training, real-time monitoring, and full PCI compliance. If you're too focused on security myths, however, you could be missing the elephant in the room, such as a server that hasn't been patched in a decade, or the fact your company has no means of detecting a breach that slips past your firewall. Join us as we review the truth behind ten pervasive security myths, and what the DBIR indicates about their veracity.
Myth #1: Cybercrime Attacks are Random
Actually, Verizon writes, "most attacks are opportunistic, indiscriminate, and exploit known vulnerabilities." Effective criminals have a lazy streak. That's why the ten most common vulnerabilities accounted for 85% of incidents in the previous year. While there were over 900 common vulnerability profiles in total, criminals love tapping into known issues with Adobe Flash, Acrobat, and Microsoft products.
Myth #2: Companies are Getting Better at Detecting Breaches
Perhaps one of the most depressing findings in the 2016 DBIR was that "the gap between compromise and detection is widening." In other words, criminals are certainly getting faster, but organizations aren't. A staggering 93% of breaches resulting in data loss were concluded in a matter of minutes or less. However, a full 7% of breaches go undiscovered for an entire year, while 80% of compromised organizations don't realize they've been breached for weeks on end.
Myth #3: Strong Passwords Mitigate Most Risks
Only 13% of security incidents involving the use of actual credentials resulted from default or weak passwords which were cracked with "brute force." Credential theft was far more common. While the data from the DBIR certainly indicates password-created risks are far higher than they should be, cybercriminals are more often gaining access to credentials through phishing attacks and other modes of theft.
Myth #4: Spam Filters are Critically Important Phishing Protection
Unfortunately, phishing attacks increased, not decreased, over the past year. Despite organizations' attempts to filter out malicious messages with better modes of email barriers, humans are still the biggest risk factor when it comes to phishing.
Even more disconcertingly, 30% of phishing emails are opened, which represents a 7% increase over the 2015 DBIR. Twelve percent of employees click on links or attachments, which can result in the download of persistent malware within seconds. Behaviorally-based training and simulation are critical means of reducing these risks in the year to come.
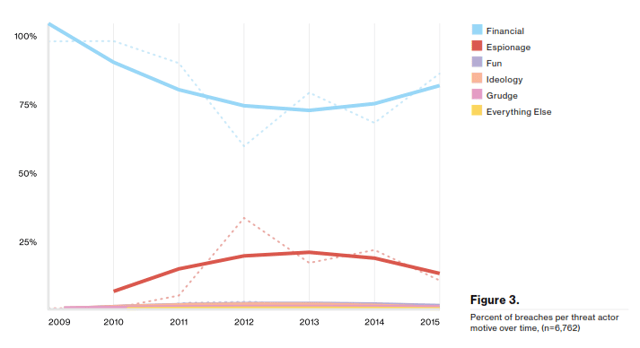
Myth #5: Attack Motive Can Vary Significantly
The vast majority of security incidents are done with a single end in mind: financial gain. Financial motivations crushed the predominance of all other primary motivations in attacks, which can include:
- Espionage,
- Fun.
- Ideology,
- Grudges, and
- Other Factors.
In fact, the only other factor which appeared in the DBIR's analysis with any statistical significance was espionage:
Myth #6: There Are Too Many Threats to Keep Up With
The information security threat vector is definitely complex and evolving. Symantec reports that over the last year, a new form of zero-day vulnerability was discovered on a weekly basis. Over the past two years, the rate at which zero-day vulnerabilities are discovered has more than doubled.
However, organizations don't need to yield to criminals. Ninety-five percent of breaches fit into a total of nine attack patterns. If organizations implement basic modes of protection such as full PCI compliance on a consistent basis, their risks are much lower.
Myth #7: BYOD is the Worst Idea in History
Bring-your-own-device (BYOD) and other forms of a mobile-driven workforce have come under active attack from security experts as a way to introduce massive vulnerabilities into an enterprise. However, Verizon DBIR reports that once again, mobile simply isn't a common attack method. None of the 100,000 incidents profiled in the 2016 report involved the exploitation of mobile errors. While this doesn't mean your employees' tablets and smartphones are fully safe, it does point to the ease of exploitation in many companies' networks.
Myth #8: Crimeware Reigns Supreme
Errors, such as clicking on a phishing link or sending sensitive information to the wrong person, are actually far more common than Crimeware. Out of the ten incident classification patterns listed in the Verizon DBIR, crimeware was actually ranked sixth. Your organization is far more likely to fall prey to miscellaneous errors, privilege misuse, physical theft, or denial of service than crimeware—but it's still a risk!
Myth #9: Health Care is the Riskiest Industry
Verizon is abundantly clear that no "locale, industry, or organization" is bulletproof. If your organization has data, it's at risk. However, the analysis of incidents on a per-industry basis did manage to bust the myth that healthcare is doomed. With just 166 incidents, health organizations faced far fewer attacks than entertainment (2,707), finance (1,368), and information (1,028).
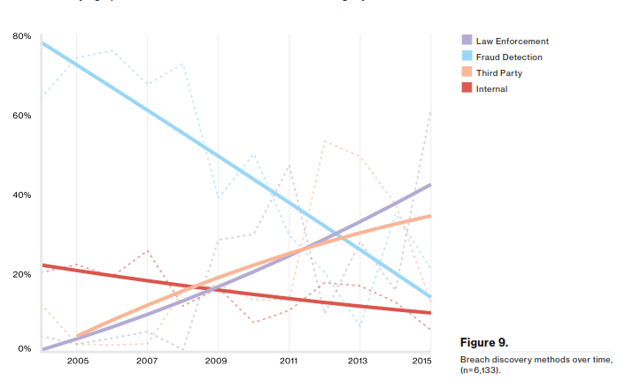
Myth #10: Internal Resources Discover Data Breaches
To be clear, internal resources, such as IT pros and team members do discover data breaches. But the chances they're behind the discovery is far less likely than a third party informing you that you've been victimized. Ranked from most common to least common, the leading methods of breach discovery are:
- Law Enforcement
- Third-Party
- Fraud Detection
- Internal
The Important Takeaway
What's the takeaway from this year's 2016 DBIR? According to IDC program director Christina Richmond, "You really have to do the basics and people still are not doing the basics." Over the next year, security decision-makers should focus on making sure they have nailed the most important core components of a risk mitigation program, which include:
- Full regulatory compliance,
- Ongoing education and training,
- Systemic vulnerability management, and
- Intrusion detection and file integrity monitoring.
File integrity monitoring allows your organization to continuously monitor changes to critical system files in a fast-changing security environment. While this year's DBIR held few surprises, it's clear building and maintaining an accurate baseline and constant vigilance are key to avoiding a data breach.
Tags:
Cybersecurity
May 19, 2016




