On May 10, 2023, the National Institute of Standards and Technology (NIST) unveiled the draft of the eagerly anticipated third revision of the NIST 800-171 standard (NIST 800-171 R3). This update brings forth significant changes, impacting organizations that handle Controlled Unclassified Information (CUI). In this post, we'll delve into the background of NIST 800-171, explore the key changes in Revision 3, and outline the implications for organizations striving to stay compliant.
Background
NIST 800-171 was initially introduced in 2016 to provide guidance for safeguarding CUI in non-federal systems and organizations. Comprising 110 security requirements organized into 14 families, the standard aimed to ensure the confidentiality, integrity, and availability of sensitive information. Revision 2, released in 2020, addressed updates and clarifications, but the evolving threat landscape prompted the need for further enhancements.
NIST 800-171 R2 vs R3 Final Public Draft
This revision of NIST SP 800-171 represents an extensive effort, encompassing data collection, technical analyses, customer interactions, redesign, and the development of security requirements and supporting information for safeguarding Controlled Unclassified Information (CUI). Throughout this process, numerous trade-offs have been carefully considered to ensure that technical and non-technical requirements are articulated with clarity and conciseness, accounting for the specific needs of both federal and nonfederal organizations.
The table below details the transition of security requirements from NIST SP 800-171 r2 to the Initial Public Draft (IPD) of Revision 3.
What notable modification distinguishes NIST SP 800-171 Revision 2 from Draft NIST SP 800-171 Revision 3?
-
Enhance clarity and customer comprehension by streamlining introductory information.
-
Eliminate the distinction between basic and derived security requirements.
-
Update security requirements and families to align with NIST SP 800-53, Revision 5, and NIST SP 800-53B moderate control baseline, incorporating updated tailoring criteria.
-
Increase specificity in security requirements to eliminate ambiguity, enhance implementation effectiveness, and define the assessment scope.
-
Introduce Organization-Defined Parameters (ODP) in selected security requirements to boost flexibility and assist organizations in better risk management.
-
Remove outdated and redundant security requirements.
-
Provide a detailed analysis of Revision 2 and Revision 3 changes, accessible through the Revision 3 publication details.
-
Develop a prototype Controlled Unclassified Information (CUI) overlay, accessible through the Revision 3 publication details.
Basic vs. Derived Security Requirements
What prompted NIST to remove the differentiation between basic and derived security requirements? The aim of FIPS 200 was to outline overarching security requirements for federal agencies, met by choosing and adapting controls from NIST SP 800-53. An unintended consequence of relying on FIPS 200 as a primary source for crafting NIST SP 800-171 security requirements was the inherent lack of specificity. Realigning the security requirements solely with NIST SP 800-53 as the singular authoritative source showed a substantial enhancement in specificity and clarity.
Organization-Defined Parameters (ODP)
With the introduction of Organization-Defined Parameters in R3, the intention was to provide flexibility similar to NIST SP 800-53 controls by granting federal agencies flexibility in tailoring controls to align with unique organizational missions or business functions and effectively manage risk.
To extend this flexibility to federal agencies collaborating with nonfederal organizations for the protection of Controlled Unclassified Information (CUI), ODPs have been selectively integrated into the requirements of NIST SP 800-171, Revision 3, aligning with their use in NIST SP 800-53, Revision 5. Once defined, ODPs become integral to the security requirement and are subject to assessment. ODPs streamline assessments by providing specificity to the requirements under evaluation, reducing ambiguity, and preventing inconsistent interpretations by assessors. Federal agencies have the option to stipulate ODPs, offer guidance on their selection for nonfederal agencies, or permit nonfederal agencies to choose ODP values autonomously.
Other Subtle Changes
To align with the NIST SP 800-53B moderate control baseline, Revision 3 incorporates three new security requirement families: Planning (PL), System and Services Acquisition (SA), and Supply Chain Risk Management (SR). Furthermore, the Security Assessment family has undergone a name change to Security Assessment and Monitoring (SA).
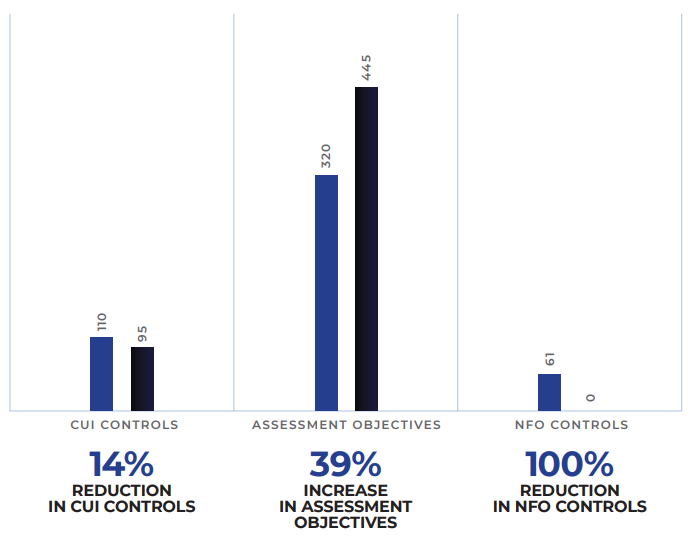
NIST also altered security control tailoring criteria assignments in response to public feedback and insights. The changes addressed concerns that certain Foundational Operations (NFO) controls, including key ones like XX-1 controls from each family, were not effectively implemented or assessed. The adjustments, detailed in Appendix E (Table 41) of NIST SP 800-171 during the transition from Revision 2 to Revision 3, resulted in a significant decrease in NFO controls and an increase in NCO, FED, and CUI controls.
Furthermore, NIST removed the mapping of the NIST SP 800-53 security controls to the ISO 27001 security. They decided to exclusively concentrate the mapping table in NIST SP 800-171, Revision 3, on NIST SP 800-53 security controls, recognized as the authoritative source for security requirements. The current focus is on updating the mapping of NIST SP 800-53, Revision 5 controls to align with ISO/IEC 27001:2022 controls.
CMMC 2.0
The remaining question becomes, how does this impact the Defense Industrial Base (DIB) and their anticipated compliance requirements to CMMC 2.0? Any contractor with a DFARS 7012 clause in their contract must adhere to NIST 800-171r2 until further notice.
How CimTrak Can Help
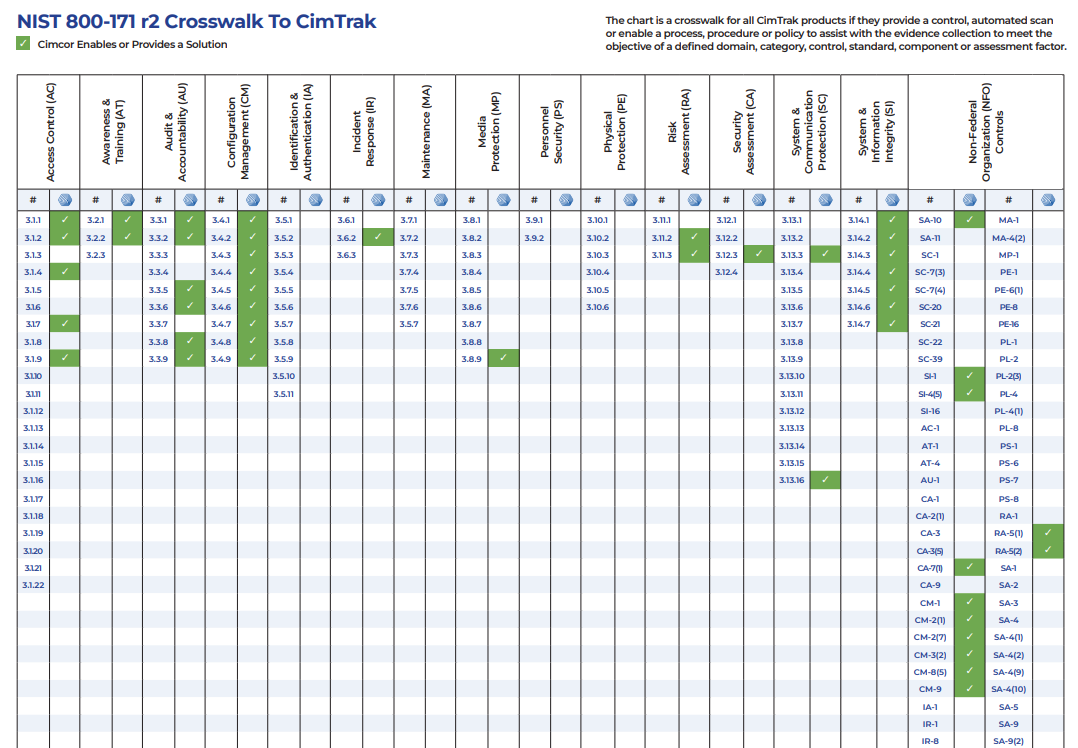
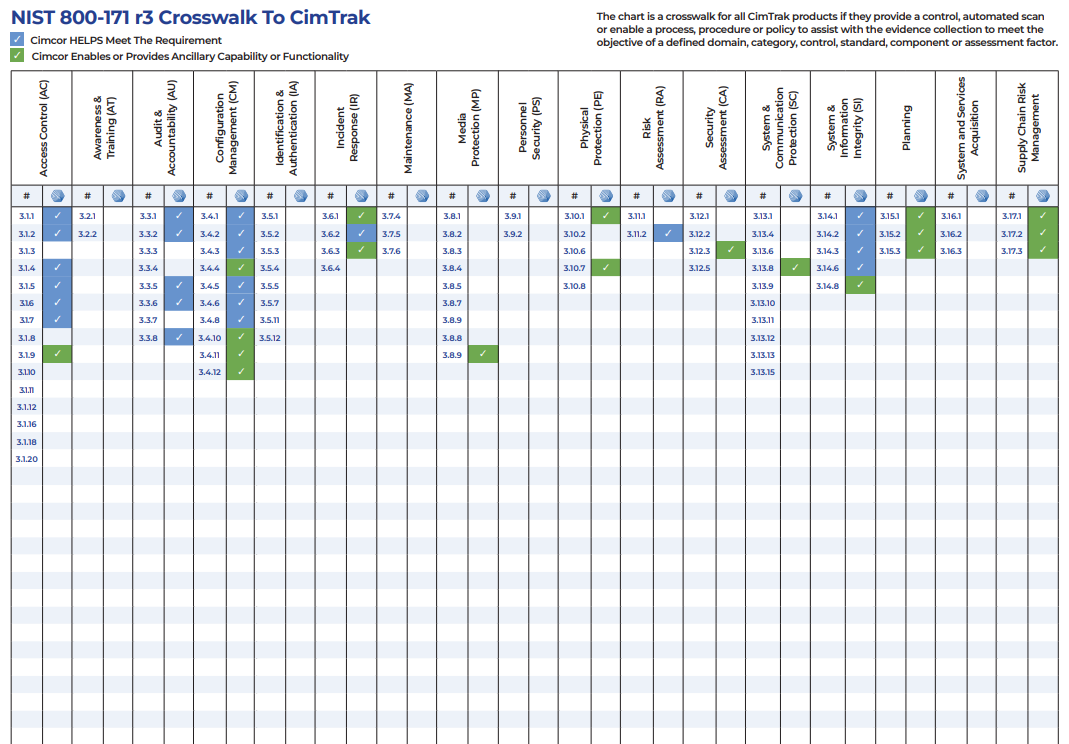
Meeting the compliance objectives of 800-171r3 and CMMC 2.0 will become a moving target in the coming months. That said, crosswalks of CimTrak integrity controls are provided for both R2 and R3 for those needing to align with either revision. These crosswalks indicate where CimTrak provides a control, automated scan, or enables a process, procedure, or policy to assist in collecting evidence to meet both requirements.
CimTrak Crosswalk with NIST 800-171 R2
CimTrak Crosswalk with NIST 800-171 R3
NIST 800-171 Revision 3 signifies a substantial evolution in the standard, demanding the attention of organizations handling CUI. With new security requirements, updated guidelines, and modified assessment procedures, staying informed and implementing necessary controls is imperative. Non-compliance can result in severe consequences, emphasizing the need for organizations to prioritize adherence to the latest guidance to protect CUI and maintain compliance obligations.
Tags:
Compliance
February 6, 2024




