The landscape of digital transactions is constantly evolving, as are the associated threats. Responding to the dynamic nature of cybersecurity challenges, the Payment Card Industry Security Standards Council (PCI SSC) released v4.0 of the PCI Data Security Standard (PCI DSS) on March 31, 2022. This new iteration replaces version 3.2.1 and introduces several noteworthy changes and improvements to address emerging threats and technologies.
A Global Standard Evolving with Feedback
PCI DSS is a global standard establishing technical and operational criteria for safeguarding account data. The release of version 4.0 is a testament to the commitment of the PCI SSC to adapt to the ever-changing landscape of payment security. Over the past three years, feedback from more than 200 organizations worldwide has been incorporated, focusing on keeping the standard relevant in the complex realm of payment security.
Key Changes and Updates
1. Emphasis on Continuous Security
PCI DSS v4.0 places a strong emphasis on security as a continuous process. The updates aim to meet the evolving security needs of the payment industry, encouraging organizations to view security not as a one-time compliance requirement but as an ongoing commitment. This is reflected in more stringent requirements for multi-factor authentication (MFA) and updated password standards.
2. New Requirements and Guidance
The latest version introduces new requirements and assigns specific roles and responsibilities for each one. This provides clarity on how organizations should implement and maintain security measures. Additionally, PCI DSS v4.0 incorporates guidance to assist individuals in better understanding the implementation of security controls.
3. Enhanced Flexibility for Organizations
Recognizing the diverse methods organizations employ to achieve their security goals, PCI DSS v4.0 introduces new options to enhance flexibility. This includes permissions for group, shared, and public accounts and targeted risk analyses to help organizations determine the frequency of certain security activities. A customized approach is also introduced, providing innovative methods for organizations to meet PCI DSS requirements.
4. Improved Verification and Reporting
Detailed reporting options have been developed to enhance verification methods and procedures. This ensures increased congruence between information reported in Compliance Reports or Self-Assessment Questionnaires and the information summarized in the Attestation of Compliance.
Transition Period and Implementation
After the launch of PCI DSS v4.0, organizations have a two-year transition period, lasting until March 31, 2024. During this time, PCI DSS v3.2.1 remains operational, allowing organizations to familiarize themselves with the changes, update reporting templates, and plan and implement necessary adjustments. Assessors can choose to undertake assessments using either version after completing PCI DSS v4.0 training.
Organizations must understand that new best practice requirements identified in PCI DSS v4.0 must be fully implemented by March 31, 2025. Until then, compliance is not mandatory, but organizations prepared to meet these new requirements can audit through them.
Summary of Control Requirements
PCI DSS version 4.0 consists of 12 requirements and three additional Appendices. Altogether, there are 280 individual controls specified across the 12 requirements and three appendices.
Ensuring PCI DSS Compliance with CimTrak
Securing sensitive data and maintaining compliance with industry standards and requirements is paramount for businesses. PCI DSS is designed to safeguard cardholder information and ensure secure processing of payment transactions. As organizations strive to meet the stringent requirements of PCI-DSS version 4, they often turn to CimTrak to provide continuous compliance and assurances that the necessary and effective controls are not only in place but operating as intended.
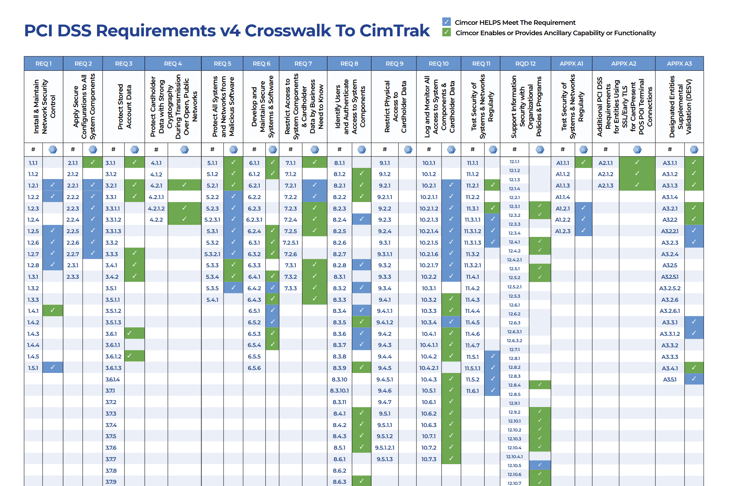
PCI DSS v4 Crosswalk to CimTrak
As a visual aid, the following crosswalk summarized the alignment of CimTrak with PCI DSS version 4.
How CimTrak Helps
CimTrak complies with the control requirements and/or offers ancillary capability and functionality to 141 of the 280 controls. Below is a summary of where and how CimTrak provides the necessary functionality to meet that control requirement.
Build and Maintain a Secure Network and Systems
Requirement 1: Install and Maintain Network Security Controls
CimTrak's File Integrity Monitoring (FIM) capability plays a pivotal role in detecting changes to critical infrastructure in real-time and determining if those changes are expected and authorized. By ensuring the integrity of security controls, CimTrak alerts administrators to unauthorized or malicious alterations, allowing for immediate rollback to a trusted baseline.
Requirement 2: Apply Secure Configurations to All System Components
CimTrak provides continuous configuration audit and assessment, scanning systems against established security baselines to verify secure configurations in line with PCI DSS requirements.
Protect Account Data
Requirement 3: Protect Stored Account Data
While not focused on data encryption, CimTrak's FIM functionality promptly detects unauthorized changes or access to files storing sensitive data.
Requirement 4: Protect Cardholder Data with Strong Cryptography During Transmission Over Open, Public Networks
CimTrak's FIM can monitor and alert on configuration changes or software managing data transmissions, ensuring cardholder data security during transmission.
Maintain a Vulnerability Management Program
Requirement 5: Protect All Systems and Networks from Malicious Software
CimTrak's FIM detects changes caused by malicious software, facilitating rapid response to potential threats. It monitors critical system files to ensure they remain unaltered and uncompromised.
Requirement 6: Develop and Maintain Secure Systems and Software
CimTrak's FIM module monitors files, registries, databases, and more, providing real-time identification of system changes. Its continuous configuration audit ensures compliance with secure configurations and hardening standards.
Implement Strong Access Control Measures
Requirement 7: Restrict Access to System Components and Cardholder Data by Business Need to Know
CimTrak monitors access and changes to files, alerting on unauthorized access or modifications. 'Monitor Reads' mode creates an audit trail of all file access.
Requirement 8: Identify Users and Authenticate Access to System Components
CimTrak's monitoring capabilities track changes to authentication configurations, ensuring robust identity and access controls.
Regularly Monitor and Test Networks
Requirement 10: Log and Monitor All Access to System Components and Cardholder Data
CimTrak establishes an authoritative baseline, providing robust monitoring and logging of all access and changes to system components for a comprehensive audit trail.
Requirement 11: Test Security of Systems and Networks Regularly
CimTrak provides continuous audits and assessments to determine if systems comply with PCI DSS and other security standards.
Maintain an Information Security Policy
Requirement 12: Support Information Security with Organizational Policies and Programs
CimTrak supports policy enforcement by monitoring systems for compliance and detecting deviations from established security policies.
Appendix A Additional PCI DSS Requirements
Appendix A1: Additional PCI DSS Requirements for Multi-Tenant Service Providers
CimTrak, as a multi-tenant solution, ensures the logical separation of customer data. It supports incident response for all customers with robust forensic details surrounding unauthorized changes.
Appendix A2: Additional PCI DSS Requirements for Entities Using SSL/Early TLS for CardPresent POS POI Terminal Connections
CimTrak verifies systems/network configurations to confirm that devices using SSL and/or early TLS remain secure.
Appendix A3: Designated Entities Supplemental Validation (DESV)
CimTrak provides PCI DSS compliance evidence, executive-level visibility, closed-loop change control, and process validation to detect and promptly address critical integrity control failures.
In Conclusion...
As organizations navigate the complex landscape of PCI-DSS compliance, leveraging advanced solutions like CimTrak becomes imperative. The benefits of continuous monitoring, file integrity monitoring, automated reporting, and enhanced security controls make CimTrak a valuable ally in achieving and maintaining compliance with PCI-DSS Version 4. Investing in robust cybersecurity solutions can help organizations meet regulatory requirements and fortify their defenses against evolving cyber threats.
Tags:

January 23, 2024