As businesses become more dependent on the cloud, naturally, new security challenges will arise.
CWPPs are specifically defined by Gartner as, "workload-centric security products that protect server workloads in hybrid, multicloud data center environments". In this post, let's dive further into the details of what they are, why they're important, and how to get started.
Cloud Workload Protection Platform Market
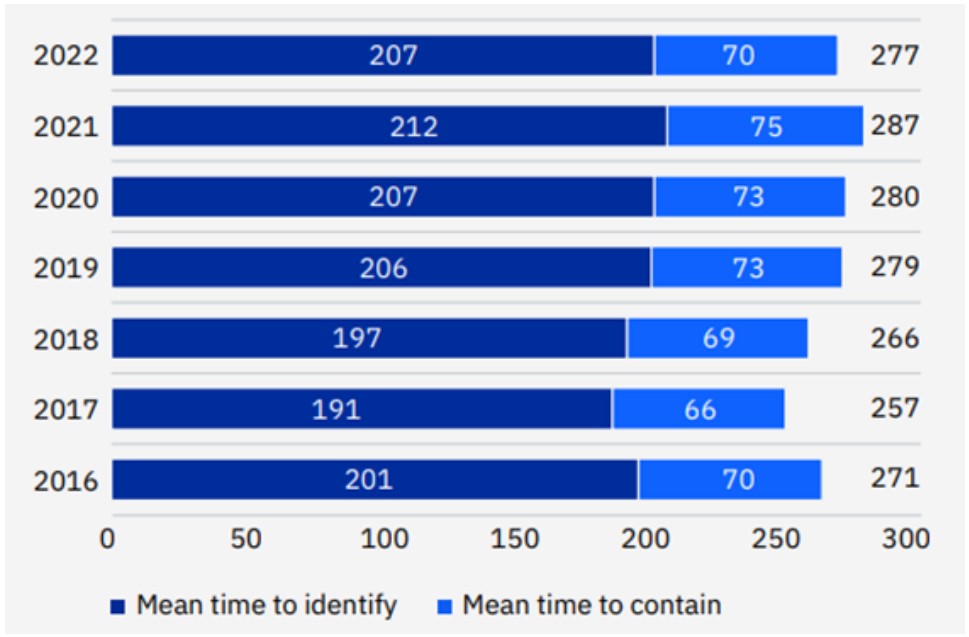
The market for workload protection controls is defined by workload-centric security protection solutions, which are typically agent-based and hierarchical by design. CWPPs provide visibility and control of server workload protection in hybrid data center architectures that span on-premises, physical and virtual machines (VMs), and multiple public cloud infrastructure as a service (IaaS) environments. Ideally, they also support container-based application architectures. The reality is that most enterprises currently have workloads distributed across a combination of all three environments which include multiple IaaS providers. CWPP offerings are built on the operational and security hygiene best practices that are foundational to every organization, large and small, and then build upon that foundation with core workload protection strategies with the identification of less critical (but also important) controls running outside of the workload. Gartner’s prescriptive guidance to the protection of server workload simplifies and prioritizes an organization’s approach to minimizing security events and the mitigation of risk, which has a drastic effect of driving the industry average of mean-time-to-identify and mean-time-to-contain security breaches of 207 and 70 days respectively down to seconds in both cases (figure 1).
Why is CWPP So Important?
As the market continues to migrate from the traditional legacy and on-premise to cloud-native, applications need to be retooled and redeveloped as the effort to accomplish this transition isn’t as easy as “copy-paste” to the cloud. Here are five things to think about when considering the importance of CWPP:
- Most best practice and compliance frameworks offer a list of controls to consider, but CWPP takes a prescriptive approach by focusing on the most important and critical controls. This approach applies not only to cloud services but also to virtual environments and on-premise operations.
- Given that most organizations have a very complex set of legacy applications, this transition is no simple feat. The functionality and security framework required for a
comprehensive security strategy does not translate directly. - Most organizations are using a mixture or hybrid of cloud services from multiple vendors for any number of reasons. Having a common perspective on the hierarchy of critical controls is essential for security professionals to know and understand. In doing so, variables will be removed and the success of security within cloud services becomes realistic.
- DevOps is a process of continuous innovation and continuous development (CI/CD) where application developers utilize workloads from various sources and locations to create and publish applications quickly and effectively. This enables DevOps to react quickly to customer needs in a short period of time.
- The concession for rapid development and application improvement means that security personnel needs a uniform and consistent approach to workload protection.
With the constant change of workload environments, lack of visibility and control, and the continuous DevOps cycle, CWPP is an ideal security framework to adopt and implement. It is prescriptive and prioritizes what controls should be classified as foundational and less critical.
CWPP vs EPP
CWPP is very different from Endpoint Protection Platforms (EPP) as CWPP is focused on the protection of workloads regardless of their location whereas an EPP is specifically focused on the protection and visibility of preventing attacks
on endpoints. However, the combination of these two provides a comprehensive and robust architecture to mitigate security risks and exposures. Cimcor’s integrity framework, CimTrak, strategically aligns its core features and functionality with both CWPP and EPP.
Implementing an Effective CWPP Solution
For the past twenty years, Cimcor has been offering IT controls to minimize the danger of security threats and breaches. Unfortunately, these foundational controls
have not received enough attention compared to less critical ones such as behavioral monitoring, host-based intrusion prevention, and a few other areas. This has resulted in an uncontrollable amount of security incidents/breaches and irresponsible IT security spending that continues to jeopardize and compromise the risk and security of IT infrastructures around the world (both on-premise as well as the cloud). Simply put, organizations need to prioritize the implementation of foundational controls where they can demonstrate the greatest ROI from both a cost and risk perspective.
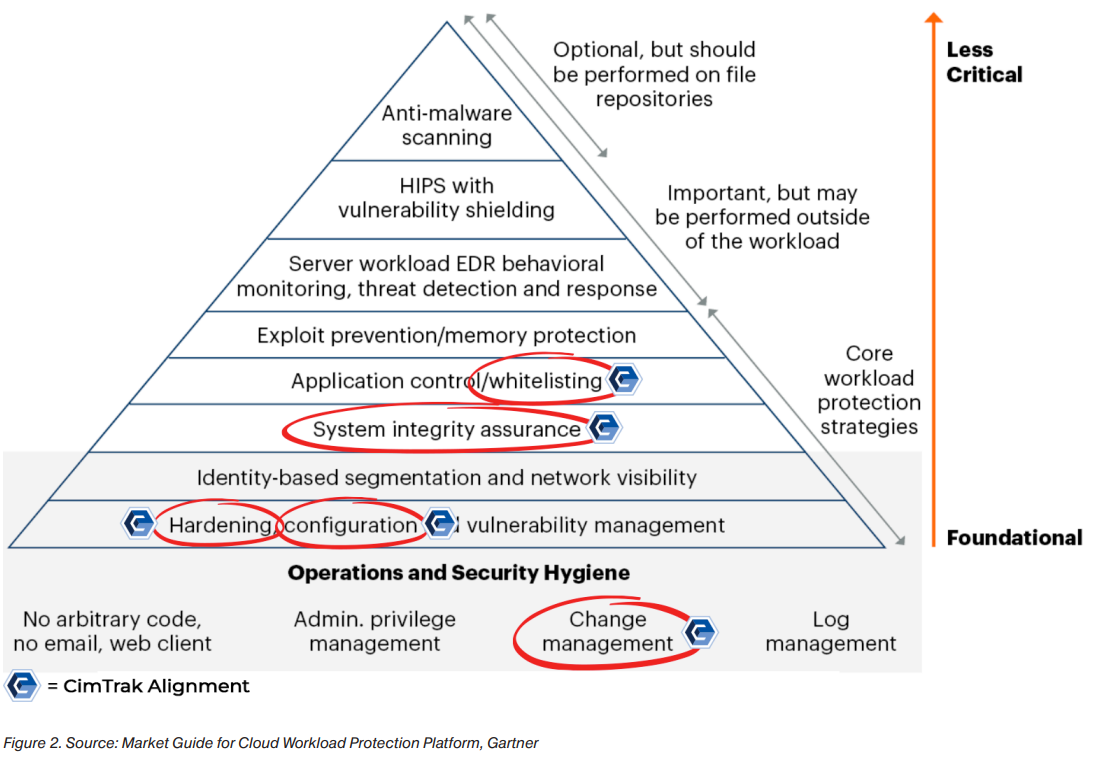
This prioritization of foundational and basic security hygiene controls is not only called out in Gartner’s CWPP hierarchy, but they are also included in almost every best practice and compliance framework such as NIST 800-53, Information Technology Infrastructure Library (ITIL), CIS Controls, CMMC, PCI, and many others.
To gain a deeper understanding of Gartner’s workload protection platform, it is important to utilize the following five control categories:
- Configuration Management
- Change Management
- Hardening
- System Integrity Assurance
- Application Control/Whitelisting
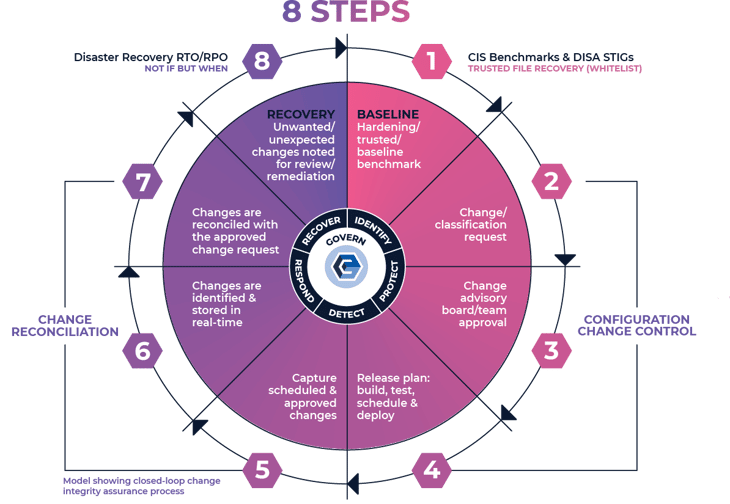
Now… taking these controls and binding them into a closed-loop workflow process, provides the unique ability to identify in real-time all unknown, unexpected, unauthorized, and malicious activity…and recover from it. Implementing the above-prescribed controls from Gartner and encapsulating a workflow process that incorporates them (Figure 3) can and will drive MTTI and MTTC from months down to days.
For more information on exactly how to implement an effective CWPP solution, download Cimcor's latest positioning paper, CWPP: Unlocking the Power of the Cloud.
Tags:

June 29, 2023




