Exabeam's LogRhythm SIEM and CimTrak
CimTrak & LogRhythm SIEM
Take control of your security posture and compliance mandates with a comprehensive set of controls that visualize, analyze, and prioritize the detection and response of targeted attacks, data breaches, and compliance drift in real-time.
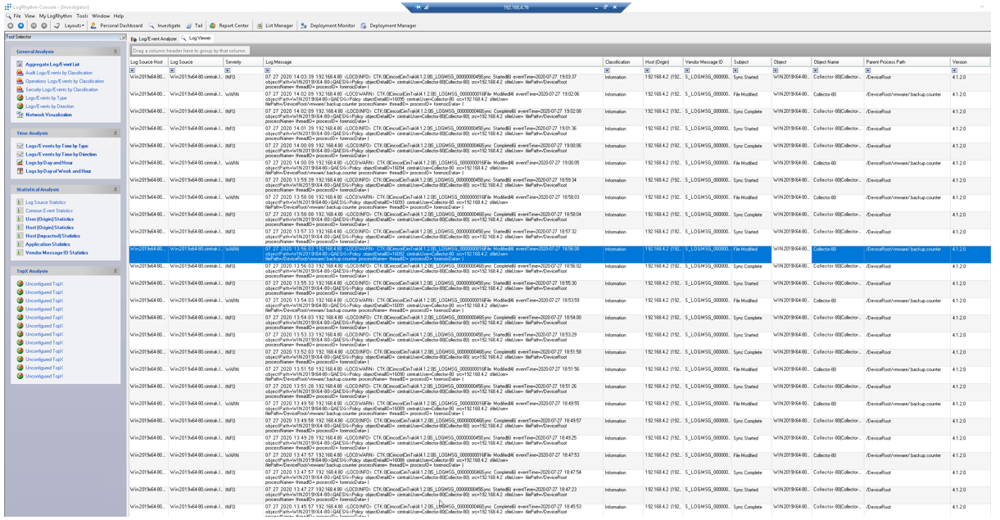
By integrating CimTrak integrity assurance data into Exabeam's LogRhythm SIEM, you can assess, investigate, and remediate unknown, unwanted, or unexpected activity across your entire enterprise, mitigating and eliminating enormous risk variables.
Through this joint integration effort, Exabeam's LogRhythm SIEM can effectively aggregate integrity data, enabling it to identify things such as zero-day breach activity which can then be manually or automatically rolled back to a previously trusted state of operation.
Add Tremendous Functionality To Your SIEM
CimTrak features that enrich LogRhythm SIEM data for incident prevention and response, forensics, and regulatory compliance include:

Detect Malicious Activity in Real-Time
Every breach begins with a change or a need for change. Measure the Mean-Time-To-Identify (MTTI) of a breach in seconds.
Next-Generation System Integrity Monitoring
Validate the integrity of infrastructure by detecting state changes against trusted baselines, CIS benchmarks, and numerous other integrity attributes.
Roll-Back & Remediation
Measure Mean-Time-To-Restore (MTTR) and Mean-Time-To Contain (MTTC) to a correct and operational state in seconds.
Prevent Change
Prevent changes entirely for those files and directories that should never change avoiding the start of a breach or problem.
Compliance
Continuous and non-disruptive compliance validation and verification with simple remediation guidance and integrated process workflow for failed systems.
"Change Noise" Suppression
Only alert on unwanted, unauthorized, and unexpected change activity through automated workflows and file allowlisting.
Change & Work Order Reconciliation
Highlight and compare observed changes against expected and authorized changes to create a closed-loop change control process.
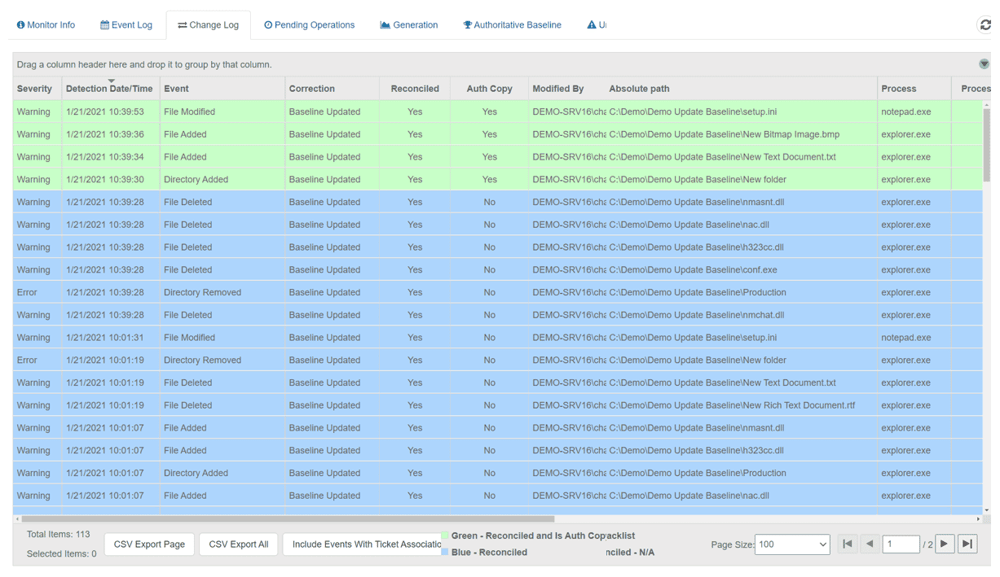
Data Forensic & Auditing
Historical evidence of all change activity is securely preserved for recovering, identifying, and analyzing the who, what, where, when, how, and why.
Ticketing System
Built-in ticketing system to enable workflow automation and control as well as the point of integration for bi-direction integration with ITSMs.
Vulnerability & Threat Management
Analyze and evaluate real-time security decisions and vulnerability risks with threat intelligence feeds (STIX/TAXII) and file reputation services.
Unprecedented Visibility
Data that gets loaded to the SIEM is what gives it value. There are a lot of bad data sources, and most data cannot easily be classified as good or bad.
CimTrak’s data provide a clear context of unwanted, unexpected, and unauthorized activity throughout your enterprise.
SIEMs are often associated with “noise.” Alert fatigue has become a major problem for organizations with SIEMS that receive an average of 17,000 malware alerts per week.
What CimTrak Provides
CimTrak provides precise and actionable data when integrity and compliance drift occur throughout your infrastructure. This unique ability reduces change noise by as much as 95% leaving concise details of unknown, unwanted, and unexpected activity.
Integrity and compliance drift is certain to occur through additions, modifications, and deletions of data throughout the lifecycle of its operation.
CimTrak can provide roll-back and remediation. Whether it’s the restoration of a failed service or a security event or breach that occurred, CimTrak can roll-back to any number of trusted and operation states as it stores in compressed and encrypted the necessary files.
Referencing CIS Controls
With so many frameworks and best practices, many often ask which is best and for what reasons. Almost all of them are very detailed, exhaustive, and descriptive telling you “what needs to be done.” However, only one is prescriptive in nature. The CIS Controls not only tell you “what needs to be done,” but they also tell you in what order they need to be considered when implementing an effective security framework.
%20(4000%20%C3%97%202000%20px)%20(8000%20%C3%97%203000%20px)%20(2).png?width=2000&height=750&name=Referencing%20CIS%20Controls%20LR%20(3500%20%C3%97%201500%20px)%20(4000%20%C3%97%202000%20px)%20(8000%20%C3%97%203000%20px)%20(2).png)
Learn More:
Download the Full Document

See How CimTrak Can Enhance
LogRhythm SIEM in Your Environment.
Mitigate security threats with the CimTrak and Exabeam's LogRhythm SIEM integration.