Zero Trust Insights
What You Don't Know About Zero Trust...
Zero Trust (ZT) isn’t anything new. It’s just a rearrangement of long-described controls within NIST 800-53 to meet the objective of a Zero Trust Architecture (ZTA). Subsequently, NIST created Special Publication 800-207, which details a ZTA with seven basic tenets to achieve success. The primary focus, as driven by the security industry, is and had been on identity and access for the purpose of mitigating the risk of exfiltrated data with Tenets #1, #2, #3, #4, and #6. However, Tenet #5 specifically calls for the enterprise to monitor and measure the integrity and security posture of all owned and associated assets.
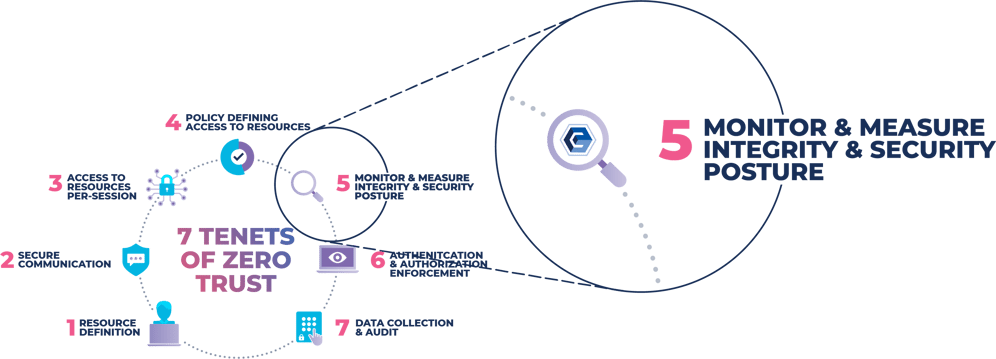
So, the question begs, what is “Integrity,” and how do you monitor and measure it? Integrity is when a system is designed, implemented, and operated in a way that can identify unauthorized deviations on a continuous basis and restore them to a previously known and trusted state of operation when unauthorized change happens. Deviations are essentially measured by anything that is added, modified, or deleted across the workload of an infrastructure, whether it’s servers, VMs, cloud configurations, containers, network devices, etc… This is accomplished through the implementation of a closed-loop workflow and ticketing system that include controls for system hardening, configuration management, change management, change prevention, change reconciliation, roll-back and remediation, STIX/TAXII feeds, and file allow-listing capabilities.
The problem that has plagued the implementation of integrity over the years has been threefold:
1. The amount of noise (alerts) due to the number of changes occurring on a daily basis.
2. The inability to scale to demanding enterprise levels.
3. The exorbitant amount of false positives.
A New Way to Approach Zero Trust
A paradigm shift has occurred. How we determine if a change is good or bad can no longer be through the lens of trying to know and understand everything bad. This approach has been and will always be reactive, allowing new and innovative malicious activities to be carried out. Managing from a state of good means having the ability to reconcile known, authorized, and approved changes which then, by default, highlights unknown changes. These unknown changes are either circumvented or malicious and are detected in real-time by the very nature of the workflow once the change is detected.
How CimTrak Can Help
The CimTrak Integrity Suite encompasses all the controls and the necessary workflow in this paradigm shift. It is easy to use, can be deployed in minutes, and can scale to the most demanding environments. By implementing CimTrak in conjunction with the other six tenets, an organization will be assured that the workload on which a ZTA is running is safe, secure, trusted, and resilient.
Try the most powerful file integrity monitoring solution.
Discover why companies like Zoom, NASA and US Air Force prevent cyberattacks with CimTrak.
