Basic information security defenses are severely lacking in many organizations, according to the 2016 Verizon Data Breach Investigations Report (DBIR). While today's cybercriminals are getting much faster at retrieving data after gaining entry to a company's network, their entry methods are rarely new or profound. The vast majority of incidents exploit known vulnerabilities. In fact, Verizon notes, "the top 10 known vulnerabilities accounted for 85 percent of successful exploits."
"There really isn't anything outstanding or brand new this year," stated Dave Ostertag, global investigations manager for Verizon. This has led to the report's unofficial tagline, a Yogi Berra quote: "It’s like déjà vu, all over again." This theme holds both positive and negative news for companies in any industry.
Clearly, successful protection requires basic measures, such as integrity monitoring software and ongoing training for personnel. Unfortunately, many of the world's biggest brands, including those who contributed data to the study, are failing to do just that. Join us as we review key findings from the 2016 DBIR.
1. No One is Safe
While Verizon states their data set isn't necessarily fully inclusive, their analysis indicates no one is safe from the risk of criminal attack, regardless of "locale, industry, or organization." While some industries suffered more incidents and confirmed data loss than others, Verizon notes the public sector isn't more at-risk than private organizations.
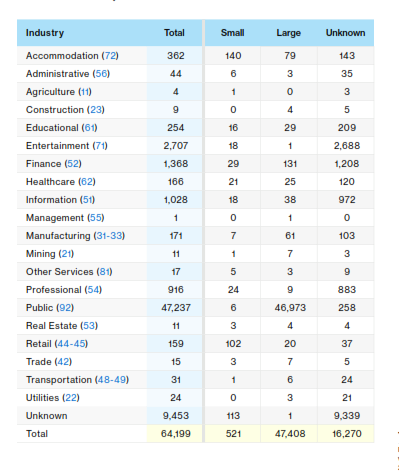
Accommodations and retail suffered the most confirmed breaches in 2016, which are detailed in the table below. The report notes this could be because these organizations process financial data and other info which is "highly desirable to financially motivated criminals."
2. Credentials are Typically Used
The vast majority of phishing schemes are designed as an attempt to steal user credentials. In addition, a staggering "63% of confirmed data breaches involved leveraging weak, default, or stolen passwords." Verizon provided additional insight on how credentials abuse stacked up by category:
- 41% of breaches involve credentials being stolen
- 48% use stolen credentials
- 13% involve default or brute-forced credentials
These numbers total more than 63% because a single breach may involve "multiple enumerations." While credential theft is far more common than default passwords, it's clear weak and default passwords can introduce an enormous amount of risk.
3. Attacks are Faster, Detection is Slower
One of the most surprising trends reported is that today's cybercriminals are faster than ever before—but victims of data breaches aren't quick to detect entry. The DBIR found that 82% of attackers completed a compromise within a matter of "minutes." Twenty-one percent of data retrieval also occurred within minutes, while 67% of criminals spent up to several days retrieving assets.
Despite the amazing speed of data breach incidents, only 25% of organizations who suffered an incident discovered the issue in a matter of days. "Unfortunately, the time to discovery is not progressing at the same rate as the time to compromise," states Marc Spitler, Verizon researcher, and report co-author. "They are innovating faster than we are." While the technology for real-time detection of negative changes to critical system files exists, not enough organizations are investing in these basic forms of protection.
4. You Might Be Too Worried About Mobile
Despite the volume of conversations among security professionals about mobile risks, mobile wasn't a major factor in the 2016 DBIR report. In fact, attacks via mobile or Internet of Things (IoT) connected devices didn't even make the report. While there certainly are vulnerabilities in mobile devices and sensors, these devices aren't yet popular attack methods.
"For those looking for proclamations about this being the year that mobile attacks bring us to our knees or that the Internet of Things (IoT) is coming to kill us all, you will be disappointed," writes the DBIR. "We still do not have significant real-world data on these technologies as the vector of attack on organizations."
Does this mean mobile and IoT should be absent from your risk management plan? Absolutely not. Spitler clarified, "We're not saying don't worry about this." However, the data indicates mobile is less popular among cybercriminals than many security experts would have predicted.
5. Phishing Recon Still Works
Phishing is still an incredibly popular and effective method of information recon among attackers. Unfortunately, Verizon's analysis indicated humans haven't grown much savvier about the risks of phishing emails.
Thirty percent of phishing messages were opened by the recipient and 12% of individuals clicked on a malicious "attachment or link" after opening the message. In the 2015 report, open rates were just 23%, and click rates were 11%. This trend could indicate security directors and staff should focus on really doubling down on education and awareness programs in the year to come to prevent credential theft.
6. People are Still Risky
Despite the vulnerabilities in technical barriers against attack, little has changed when it comes to the human side of information security. PCI compliance standards require clear policy and training programs; however, humans still account for the largest proportion of security incidents.
The DBIR indicates that 26% of human mistakes involve sending "sensitive information to the wrong person." Phishing is also an ongoing, immense vulnerability and occurs on a regular basis. While it's unlikely many companies are truly overlooking security awareness programs, there could be a need for a major shift in how companies approach training in 2016 and 2017. Employees aren't just your biggest risk, they're also your first line of defense.
7. Know Your Environment
Ninety percent of incidents that result in data loss are due to just ten vulnerabilities. Sure, cybercriminals are getting smarter and more efficient all the time. However, if their targets have wide-open vulnerabilities, such as long-outdated patches, why should they work harder or smarter?
Ultimately, this trend is great news for organizations in the year to come. By focusing on those flaws which result in the majority of data breaches, you can significantly reduce your risk of attack.
The Ultimate Message of the 2016 DBIR
If Verizon's team had to communicate a single message to security and information technology professionals after the release of the 2016 DBIR, what would it be? Per Christina Richmond, program director for Worldwide Security Services at IDC, it's that "You really have to do the basics and people still are not doing the basics."
There's certainly a relief and a sense of clear direction in the 2016 DBIR results. There hasn't been an explosion of complex new attack methodologies or strange patterns. By investing in the core components of an information security program such as file integrity monitoring, education, and other aspects of PCI compliance, organizations can significantly mitigate their risks.
CimTrak is a comprehensive solution for security and compliance and is not dependent on the most recent trends in the attack vector to operate effectively. With automated detection processes, flexible response options, and auditing capabilities, it's among the leading options for assurance and security. To learn more about CimTrak, click here.
Tags:
Cybersecurity
May 11, 2016




