Artificial intelligence (AI) works via a set of probabilities. When an AI algorithm provides a recommendation, under the hood, the algorithm will make a determination such as "this file has been classified and has a 29% chance of being malware". What is the suitable threshold to raise concerns to the security engineer? 40% chance? 90% chance? The AI is never 100% sure if something is good or bad unless it has already seen it.
All AI is based on machine learning algorithms. This means that to classify a piece of information or make a recommendation, it must be trained on a training dataset of historical information. This entails training the machine learning (ML) algorithm on a training dataset of old or previously seen malware in the cybersecurity field. The ML algorithm attempts to create a model that can accurately classify this old malware with a high level of accuracy (high probability of classifying the historical malware correctly). This is an incredible feat of engineering, but this is also the Achilles Heel of AI.
AI does a great job of classifying information that it has been trained on and even information similar to data that it has been trained on. However, it often does a terrible job of classifying brand-new and novel or unique techniques. So, if there is an entirely new piece of malware created and not based on old malware techniques, then it is highly likely that the AI will not correctly detect if anything is wrong. Another concern scenario is that, sometimes, hackers target a specific organization. In this case, every step by the hacker is custom… once again bypassing most AIs because it will not be similar to anything it has been previously trained on. In other words, advanced Zero-Day attacks and customized attacks will very likely bypass detection by even the best AI algorithms.
Never trust, but always verify!
In contrast, the precise, deterministic, evidence-based method implemented by a System Integrity Assurance solution is effective both for known threats, new threats, and zero-day attacks. An AI will assume that the file or change is good unless something bad is identified via an AI algorithm and has a "probability of malware" that exceeds a certain confidence threshold. System Integrity Assurance does just the opposite. It will always assume that the file or change is 100% invalid/bad unless a clear audit trail provides non-repudiation data/evidence. The bottom line - AI will catch new malware and unexpected changes "sometimes," and System Integrity Assurance will catch new malware and unexpected changes "all the time."
CimTrak is System Integrity Assurance
The core mission of CimTrak is to identify changes and categorize those changes as good or bad. This is done based on a zero-trust-based philosophy. If there is not a clear audit trail related to the change, it will be considered harmful. The change can be classified as good if a clear audit trail is found.
In CimTrak, this audit trail is based on digital signatures, authoritative baselines based on one-way hash algorithms, hash-based allowlist technology, and a workflow that has coupled the necessary detective controls to create a closed-loop environment for change.
This means that when CimTrak indicates that a file is "good," it is definitely good, and if it indicates that the file is "bad," that means there is no "proof" that the file or the change is authorized. This is a very deterministic and transparent way of differentiating good changes from bad.
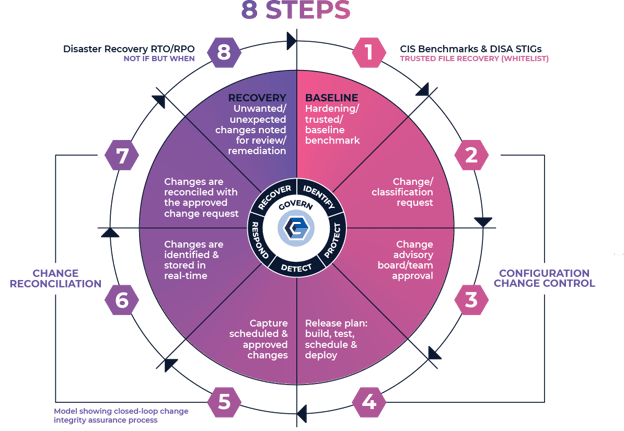
It is invaluable to users to know, without a doubt, if a change is authorized or not. If a new piece of malware is created today and targeted to a system protected by CimTrak, it would detect it. Why? Because there is no proof, there is no audit trail for that malware that would be classified as unauthorized.
The result is a clear, binary view of the disposition of changes.
CimTrak identifies, prohibits, and remediates unauthorized modifications of files, directories, and configurations and uses the same methodology to manage users, groups, policies, active directories, database schemas, cloud configurations, hypervisors, network devices, and more…
Complicate to profit, simplify to results!
The importance of change control can be seen in several best practices and compliance mandates ranging from NIST 800-53, HITRUST, PCI DSS, HIPAA, ITIL, CIS, CMMC, and dozens of others. Change control and configuration management have even been linked to statistics stating that 91% of all security breaches could be autodetected if these controls were in place and set up correctly.
All security issues start with a change or a need for change.
So, what does this mean relative to something as specific as ransomware? Currently, the industry is addressing the symptom and not the problem. Organizations are focused on the topic of how they must remediate when critical files have been encrypted/changed (symptom) as opposed to detecting and preventing the malicious payload from being delivered and installed (problem), which by definition is a change (addition/modification/deletion) that is not authorized.
Don’t get me wrong, remediation is essential. Still, it is the last resort of a workflow that follows the five functional requirements of the NIST Cybersecurity Framework (CSF) of: Identify, Protect, Detect, Respond, and then Recover if and when necessary.
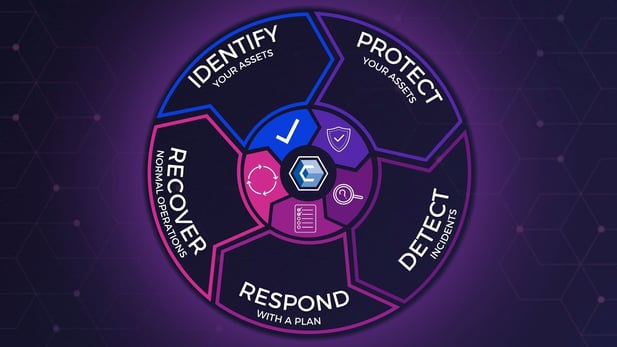
Prepare for Unexpected Changes
Utilizing a Nex-Gen FIM software that supports a Zero Trust strategy is critical in ensuring the integrity of your IT infrastructure. Rather than depending on AI in the cybersecurity sector where intellect on new and developing threats may be spotty, requiring regular authorization and verification across all users and devices is essential to protect yourself from potential threats.
CimTrak offers you the ability to quickly manage unexpected changes in your infrastructure through detailed alerts when changes occur and allows you to automatically roll back those changes. To learn more about what you need to implement an effective Zero Trust strategy in your environment, download the Missing Components of Zero Trust report.

April 25, 2023




