For years, big-name FIM vendors have stretched the truth—selling their tools as File Integrity Monitoring (FIM) solutions when in reality, they provide little more than File Monitoring.
This led to security teams using these tools purely to satisfy compliance requirements while treating them as shelfware and ignoring their alerts. Thankfully, things are changing.
Today, next-gen tools deliver the full value proposition required for FIM. In the last article, we explained how next-gen FIM differs from legacy FIM and touched on the security and compliance benefits it provides.
This article will take things a step further and cover the best practices and use cases security teams should expect to realize from a next-gen FIM tool.
Next-Gen File Integrity Monitoring Best Practices
If you’re just reviewing high-level vendor messaging, it can be difficult to tell the difference between next-gen and legacy FIM. However, when you look closely at features and capabilities, the difference becomes clear.
The table below shows how legacy tools compare to next-gen FIM solutions:
Legacy FIM |
Next-Gen FIM |
||
|
Basic file monitoring |
File and system integrity monitoring |
||
|
Lots of noisy alerts |
Cuts irrelevant change noise by 95% |
||
|
Uses a denylist to identify malicious changes |
Uses a denylist, allowlist, and trusted file registry to uncover malicious activity without swamping analysts with alerts |
||
|
Resource-intensive and relies on daily active scans |
Detects change in real-time and barely registers on the resource monitor |
||
|
“Shelfware” that’s usually only present to satisfy compliance requirements |
Fundamental to maintaining real-time system integrity across corporate IT environments |
If you’re reviewing a FIM tool and it doesn’t provide integrity monitoring and enforcement… It's a legacy FIM tool. On the other hand, if it provides genuine file integrity checking, verification, and enforcement for all files and data—without creating unnecessary noise—it’s a next-gen FIM tool.
Use Cases for Next-Gen FIM
It’s all well and good to look at the functionality of a next-gen FIM tool… but how exactly can they be used to improve outcomes and reduce security risk?
There are many use cases for next-gen FIM tools in cybersecurity and IT. Some of the most commonly recognized include:
- Detect Malicious Activity. Note the word malicious. Unlike legacy tools, next-gen FIM can distinguish between legitimate and potentially dangerous changes, reducing false positives while alerting security teams to changes relating to critical files. This helps security teams identify and respond to security incidents before any serious harm occurs.
- Compliance. FIM is an accepted requirement for prominent compliance frameworks, including PCI-DSS and HIPAA. As we’ll see later in this article, next-gen FIM goes far beyond the basic compliance benefits of legacy tools to help satisfy a high percentage of controls across many major cybersecurity compliance frameworks and standards.
- Identify Accidental Change. Accidental changes to configuration settings and critical files create vulnerabilities. FIM helps security teams identify and roll back these dangerous changes before they can lead to harm.
- Verify Updates. FIM tools make it easy to verify patches have been installed correctly across multiple systems by comparing their file checksum against a known and trusted baseline. This avoids situations where Patch Tuesday creates thousands of alerts that can’t be triaged—instead, legitimate patches are ignored, while only patches that can’t be verified need to be investigated.
- Maintain System Integrity. By detecting changes from a trusted baseline, FIM tools help organizations maintain system integrity by preventing or rolling back unwanted changes. Not only does this save manual effort, but it also remediates dangerous changes much sooner than would be possible using a legacy FIM tool.
- Forensic Analysis. FIM tools help security analysts understand the events leading up to an incident by providing a full record of changes over time, including the accounts used. This provides crucial context during post-event analysis, helping security
Next Generation FIM Automates Compliance and System Hardening
Next-gen FIM tools automate the process of achieving and maintaining compliance with frameworks like PCI-DSS, HIPAA, NIST 800-171, CMMC, and more—as well as system hardening best practices like CIS Benchmarks and DISA STIGS. It does this by:
- Building requirements of all applicable frameworks into the trusted baseline.
- Continually monitoring all files and configurations against the baseline.
- Raising alerts for issues or misconfigurations and providing evidence and guidance to resolve them.
This makes it easy for cybersecurity teams, asset owners, and IT teams to quickly identify and resolve any issue that brings the organization out of compliance with an applicable standard.
This mostly automated process provides the monitoring, enforcement, and audit trail needed to demonstrate compliance at any time—not just during an audit. This greatly reduces the time and resources required for compliance activities, freeing them up for higher-value functions.
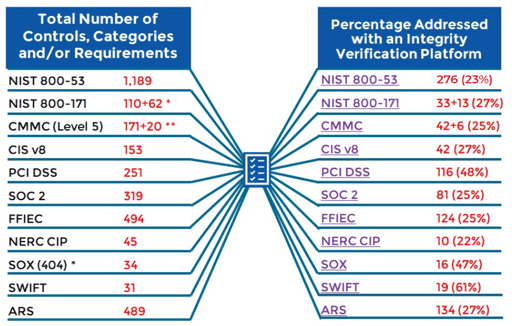
Mapping Next Generation FIM to 9 Compliance Frameworks
Next-Gen FIM can help any organization reach and maintain compliance with any framework. Simply update the trusted baseline with all compliance requirements and action any alerts raised.
To give an idea of how valuable integrity verification can be to a compliance program, the image below shows how it maps to nine common frameworks.
Mitigate Security Risks with Next-Gen FIM
Next-Gen FIM provides security functionality that goes far beyond what the industry has come to expect from FIM tools. Some of the most immediately apparent benefits include:
- Blocking most threats at their source.
- Instantly ‘healing’ files and settings to their trusted state.
- Getting deep insight into the state of any asset or system.
- Cutting incident response time with thorough forensic evidence.
- Reducing remediation time and costs.
However, as valuable as these benefits are, there’s far more to the story. For a full rundown of what next-gen FIM is, how it works, and the benefits it provides, visit our new Next-Gen FIM resource page.

May 9, 2023




