In our last article, we made the argument that it’s time to stop placing all the onus for protecting against supply chain attacks on buyers.
Even the biggest buyers—government agencies, critical infrastructure providers, and so on—simply don’t have the time or resources to vet every one of their suppliers' security thoroughly.
Instead, it’s time to regulate technology vendors.
So far, we’ve laid out three proposed requirements for them:
- Follow an agreed framework for Supply Chain Risk Management (SCRM)
- Focus on baseline integrity
- Establish closed-loop change control
Now it’s time to discuss our fourth—and arguably most important—proposed requirement for technology vendors.
Requirement #4: Adopt Resiliency-Focused Security Operations
Most organizations model security operations using a perimeter defense and recovery model. Simply, they aim to fortify their perimeter with security technologies and then invest heavily in recovery when a breach occurs. As EO 14028 explains, this model is outdated for two reasons:
- Network traffic and assets are increasingly positioned outside the corporate firewall, making perimeter defense impractical and ineffective.
- Reactive-focused security operations are expensive and too slow to prevent the loss of sensitive data or disruption to critical assets or infrastructure.
Instead, technology vendors (or any organization that needs robust cybersecurity) should implement resilient security operations that focus on prevention and automated recovery. Under this model, vendors would invest resources upfront to establish a trusted baseline for their environments and enforce security configuration of assets in line with a best practice such as DISA STIGs.
Through this—and the capability to automatically return to their trusted baseline—vendors would drastically reduce the time and cost of recovering from a network intrusion when (not if) one occurs.
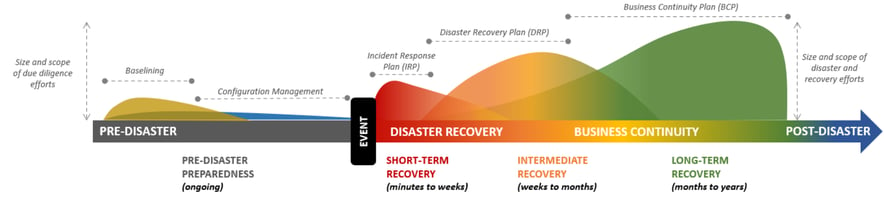
Reactive vs. Resilient Security Operations
The diagram below shows the difference between reactive- and resiliency-focused security operations.
Reactive-Focused Security Operations
Resiliency-Focused Security Operations
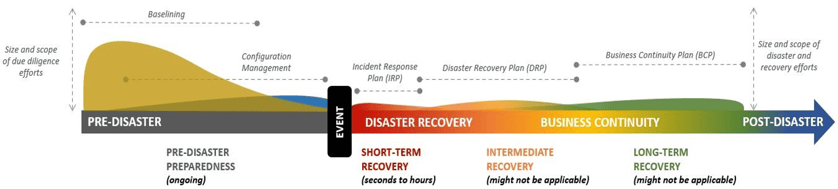
The difference is stark. While resiliency-focused operations require a greater upfront investment of time and resources, they enable substantially improved response outcomes in the event of a breach.
Recovery efforts are typically measured in minutes and hours rather than months and years, as with reactive-focused operations. This enables the organization to minimize the cost of response activities and the breach's negative impact, including on third parties and customers.
Combined with our first three recommended requirements, this increased focus on resilience in security operations would dramatically reduce the impact of successful software supply chain attacks.
However, there’s one more thing regulators should consider when regulating technology vendors.
Requirements for Technology Vendors Should Be Prescriptive
A strong foundation in the four controls we’ve suggested would help technology vendors protect against the dangers of supply chain attacks. However, regulations should go beyond telling vendors what to do by also telling them how to do it—i.e., they should be prescriptive rather than descriptive.
Most cybersecurity frameworks tell organizations what to achieve but don’t provide guidance on how to achieve it. This creates what Tony Sager, SVP and Chief Evangelist at the Center for Internet Security (CIS), calls a “special snowflake” approach that forces each organization to find its own solution:
“Compliance requirements are what I call cosmic frameworks. They proclaim ‘thou shalt achieve this,’ but aren’t prescriptive about how to do that. It creates an industry of tea leaf readers trying to interpret requirements, which is great for job security but very poor for business outcomes.”
To protect the U.S. from supply chain attacks, requirements for technology vendors must be prescriptive, laying out a single best practical route to effective SCRM. This will support technology vendors to improve the security of their products while also making it easy for them to ensure (and prove) their compliance with new regulations.
Protecting the U.S. From Supply Chain Attacks
Our new white paper, ‘Protecting the U.S. From Supply Chain Attacks,’ explains why technology vendors are frequently the weak link that allows criminal and state-sponsored hacking groups to access sensitive data and systems, conduct espionage, and disrupt operations. To protect against the dangers of supply chain attacks, technology vendors must have a legal obligation to uphold a minimum standard of SCRM.
Download the report to learn:
- Why President Biden’s Executive Order and new publications from NIST and CISA aren’t enough to protect the U.S. from supply chain attacks.
- What consequences a supply chain attack could have for federal agencies, state governments, and even private organizations.
- The risk posed by unregulated technology vendors and why it’s unrealistic to expect buyers to shoulder the burden of vetting every supplier’s SCRM capabilities.
- Our proposed approach to address supply chain risk in the U.S. and how regulators could structure a legal framework for SCRM.

April 19, 2022




