For all the grandiose terminology and technical challenges it poses, Zero Trust is a logical extension of cybersecurity concepts that have been around for decades.
In the past, we’ve highlighted elements of cyber hygiene that date all the way back to the original publication of ITIL in the 1980s. We’re not going quite that far back today—but there’s no doubt that Zero Trust stands on the shoulders of concepts that are far from new.
Start from the Beginning
The diagram below has been issued repeatedly by Gartner for years, and has remained largely unchanged since 2018:
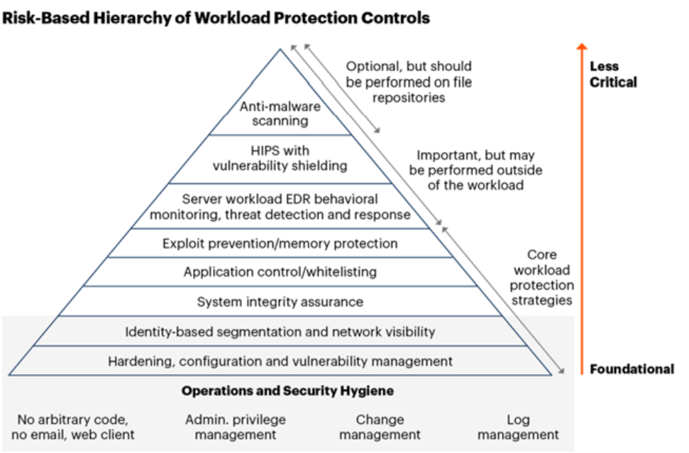
Notice that “critical, cutting edge” tools—many of which rely on denylisting—are considered the least important factors in reducing cyber risk, while the basics are considered essential. These basics boil down to concepts that everybody in cybersecurity learns within their first year:
- Least privilege access management
- System integrity
- System hardening and configuration management
- Vulnerability management
- Network visibility and monitoring
- Change and log management
In addition to being essential components of any cybersecurity strategy, these concepts lie at the heart of Zero Trust. The only way to eliminate reliance on assumed trust is to have complete oversight of an IT environment and control over what is allowed to happen within it.
Eliminating Trust In Practice
To put this more simply, a true Zero Trust Architecture requires an organization to:
- Know everything that should be allowed to connect to corporate infrastructure—and disallow everything else.
- Know the expected, secure configuration state of all assets, devices, applications, cloud instances, infrastructure, etc.—and disallow access if these states aren’t met.
- Monitor everything that happens to or within a corporate resource or environment—and block anything that isn’t expressly allowed.
- Ensure all subjects and assets remain in the most secure state possible—i.e., by enforcing secure configuration and remediating vulnerabilities.
This requires a full-stack approach that combines widely understood Zero Trust access and authorization controls with more fundamental integrity assurance and cyber hygiene capabilities to address the four layers mentioned earlier.
|
Identity |
Device/ Workload |
Access |
Transaction |
|
|
User |
User authentication |
Identify and verify user integrity |
Enforce least privilege to users |
Manage transaction / content security per session |
|
Application |
DevOps authentication |
Identify and verify application integrity |
Enforce least privilege to applications |
Manage transaction / content security per session |
|
Infrastructure |
Admin authentication |
Identify and verify device integrity |
Enforce least privilege to infrastructure |
Manage transaction / content security per session |
|
NIST SP 800-207 Tenet(s) |
#1, #3 |
#1, #5, #7 |
#4, #6, #7 |
#2 |
The Missing Components of Zero Trust
Our report, ‘The Missing Components of Zero Trust,’ explains what Zero Trust really is, examines some significant gaps in existing guidance, and details the most important concepts and capabilities required for an effective Zero Trust Architecture.
Download the report to learn:
- The Core Principles and 7 Tenets of Zero Trust.
- How the Zero Trust strategy and architecture eliminate implicit trust.
- How to elevate your security posture and avoid making the most common Zero Trust mistakes.
- The answer to the question, "Does Zero Trust actually work?"
Download your free copy today:
Tags:
Zero Trust
August 2, 2022




