How many cybersecurity service providers are there in the United States? There are an estimated 3,500 vendors in the US alone.
If you are on the hunt for a new cybersecurity service provider, you may be trapped in decision paralysis. Thousands of vendors cannot possibly be created equal, but how do you determine which service providers are capable of providing the services you require and which are not?
This post will walk you through the four simple steps you can take to help choose the right cybersecurity service provider for your business.
What Does a Cybersecurity Service Provider Do?
This post aims to provide you with the steps needed to choose your cybersecurity service provider, but before we can do that, we need to answer some baseline questions. First, what is a cybersecurity service provider?
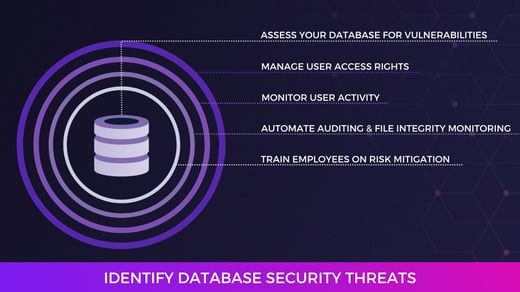
A cybersecurity service provider (CSSP) helps your organization defend against and respond to cyber-attacks. Services vary by provider, but some common services include assistance with data governance, vulnerability assessment, system hardening, cloud security, and system integrity assurance.
Your cybersecurity provider may offer these services utilizing software such as CimTrak. CimTrak provides software used by CSSPs that support the industries of finance, healthcare, education, manufacturing, and more.
In the modern age, cybersecurity efforts are more vital than ever. The average breach costs $3.86 million. On average, it also takes 287 days post-breach to detect and contain the threat. But breaches cost more than time and money.
Cybersecurity breaches also result in lost trust, lost sales, and non-compliance issues. These challenges are some of the reasons why your business needs to stay on top of its cybersecurity processes. Finding the right cybersecurity service provider is an excellent way to keep your company’s data secure.
Step 1: Determine Digital Transformation Priorities
The first step you should take when looking for a cybersecurity service provider is to examine your business processes and priorities related to data and technology. Start by establishing a baseline of where your organization is right now. What applications are you using? What does your current IT infrastructure look like? Is your work environment on-site, remote, or hybrid?
Once you have a clear picture of your current data and technology systems and processes, ask yourself where you see your business heading in the next five to ten years? Consider any new applications you may need to implement and upcoming changes to your IT infrastructure and work environment.
It’s important to note that migrating applications and making changes to your infrastructure can open your business up to new security risks.
Armed with this information, you will be able to select a cybersecurity service provider capable of supporting your business now and in the future.
Step 2: Establish Desired Cybersecurity Standards
After you’ve established your data and technology structure now and in the future, you may want to take a moment to determine the cybersecurity standards your organization needs to meet.
Consider the IT security and compliance standards most relevant to your industry. This step is especially important if your business operates in healthcare, education, or finance.
Build a list of the standards you must comply with and include any additional internal standards you want to meet. This list will help you narrow down your cybersecurity service provider search as you’ll want to partner with a provider who is experienced in the standards you need and want to follow.
Your third step is to consider the services you need your provider to offer.
Step 3: Consider Necessary Services
Establishing your exact needs upfront may be able to prevent a provider partnership that does not offer you the maximum benefit you could achieve from a CSSP.
Consider features such as real-time automated detection, dynamic version control, immediate change reconciliation, and rights denial. Ensure the cybersecurity service providers you are considering employing a software solution capable of handling all these things and more.
You will also want to consider the devices you need assistance with from your cybersecurity service provider. Consider devices like:
- Servers
- Workstations
- Network devices
- Point of sale systems
- Cloud services
Ensure the service provider you partner with has the software and experience necessary to manage your cybersecurity needs appropriately.
Step 4: Research Providers
Once you’ve completed steps one through three, you are ready to take the final step: Researching providers.
As we discussed, you will need to find a provider capable of providing the support you need and the ability to shift their approach to meet your changing needs as data and technology solutions shift in the future.
You may also want to research each company’s incident response time and track record. Set reasonable expectations for these and avoid partnering with companies that don’t meet those standards.
Lastly, you may want to read reviews or testimonials from real customers. Customer reviews can be the best way to get a sense of how it is to work with the provider and will help raise any red flags that might not have come up in your earlier research efforts. These four steps give you the information needed to make the best decision concerning your cybersecurity service provider.
Working with a Cybersecurity Service Provider
Once a provider is selected, you’ll have a conversation to ensure you are in sync related to security, compliance, and operational needs. If your provider uses CimTrak, you’ll proceed with the following steps:
- See CimTrak firsthand in the form of a demo. At this stage, you can discuss industry and business requirements and explore how your CSSP, with the help of CimTrak, can meet them.
- Activate your free trial of CimTrak. You can work directly with a Cimcor engineer at this stage to ensure a seamless installation and transition.
CimTrak users can see advantages including a 95% reduction in change noise, proactive cyberattack prevention, file integrity monitoring with system integrity assurance, and more. We have experience working with clients across multiple industries, including financial services, healthcare, utilities, government, education, and more. Schedule an instant preview of CimTrak today to see our solution in action and see if CimTrak is the right software for your organization.
Tags:
Cybersecurity
September 1, 2022